Understanding IAM Boundaries in AWS Beyond Least Privilege
A deep architectural guide to IAM boundaries in AWS, exploring permission ceilings, constraint-based design, and failure-tolerant identity governance.

20 min read
There’s a comfortable fiction that many cloud architects still cling to: the belief that implementing least privilege equates to achieving security. We scope IAM policies down to the precise actions and resources. We run access analyzer scans. We even add time-based conditions, thinking we’ve done enough. But in modern cloud environments where automated pipelines assume roles, ephemeral services invoke others, and human identities blur with machine ones, least privilege alone is no longer the shield we believe it to be.
The harsh truth? Many breaches don’t happen because a role had too many permissions. They happen because the right combination of narrow permissions, misaligned trust relationships, and absent boundary controls created an invisible path to escalation. A Lambda function scoped only to s3:PutObject might be harmless until you realize it also has permission to assume another role, invoke an inline function, or write to a CI/CD bucket that deploys production infrastructure. The role was “least privilege” in isolation, but in context, it was a loaded gun left on the table.
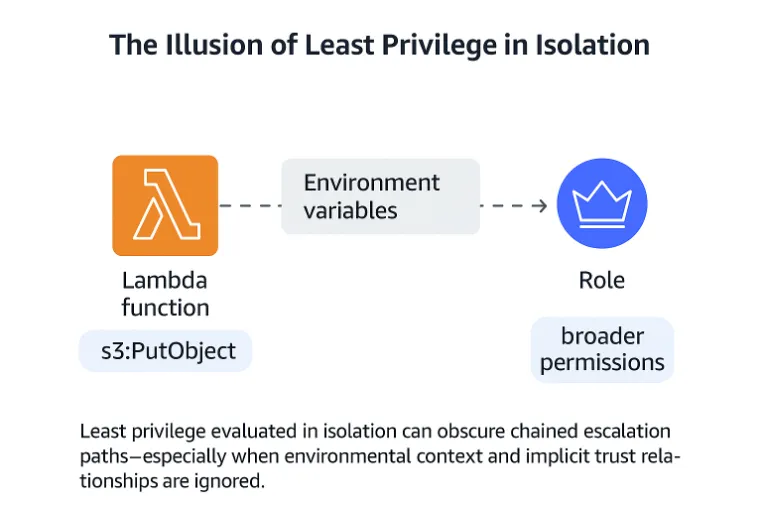
In AWS IAM, access is never evaluated in isolation. It is the sum of identities, policies, resources, conditions, and boundary constraints,each layered interaction capable of producing emergent, and sometimes dangerous, behavior.
To master IAM in AWS today goes beyond crafting tightly scoped permissions. Rather, it is architecting failure boundaries to define what must not happen, even if all other conditions align. And to do this, we must move beyond least privilege. We must understand, deploy, and engineer with IAM boundaries: permission boundaries, session policies, service control policies, and the invisible walls between what should be possible and what must never be.
In this post, we will explore what it means to construct IAM boundaries intentionally. You will see it not as a compliance checkbox, but as a security primitive. We will unpack the limitations of least privilege, the mechanics of permission boundaries, and the architecture of constrained escalation all with one goal in mind: to ensure that when things fail, they fail safely.
I. The Concept of IAM Boundaries: A Layer Deeper
To truly grasp IAM boundaries in AWS, we must first disabuse ourselves of the notion that an IAM policy is a fixed wall of permissions, a linear document granting or denying access. In truth, IAM policies operate as compositional inputs in a larger decision graph where context, inheritance, identity federation, and conditional constraints all converge.
AWS IAM boundaries are not a single feature. Rather, they are a set of architectural instruments designed to restrict or constrain what identities can do, even when their own policies, or the policies of the resources they interact with, suggest otherwise.
At the heart of IAM boundary logic lies a distinction that is often misunderstood: the difference between what an identity is allowed to do and what the system is engineered to allow under all possible permutations of context.
Consider the following constructs in AWS:
- Identity-based policies – These are attached directly to IAM users, groups, or roles. They define the what of access: what actions, on which resources, under what conditions.
- Resource-based policies – These are attached to AWS resources like S3 buckets, Lambda functions, or KMS keys. They define who can access the resource and under what constraints.
- Session policies – These are dynamic, often temporary policies passed during role assumption. They act as ephemeral overlays, temporarily constraining permissions even if the assumed role’s policy is more permissive.
- Permissions boundaries – Perhaps the most misunderstood construct, boundaries function as a ceiling rather than a floor. They do not grant permissions but define the maximum set of permissions that a role or user may exercise, even if their identity policy is more expansive.
- Service Control Policies (SCPs) – Within AWS Organizations, SCPs act as the outer perimeter. They define the absolute upper bound of what any identity within an account or OU can perform, regardless of other policy types.
When AWS evaluates whether an action is permitted, it doesn’t consult a single document. It performs a multi-step intersection of the principal’s identity policy, the resource policy, any applied boundary or session policy, and organizational SCPs. The action is only allowed if all these layers independently affirm the request.
IAM boundaries, therefore, are not just defensive mechanisms. They are proactive constraint systems that let you use permission geometry to shape and limit what identities can do.
A principal with iam:PassRole permissions might appear benign until you realize they can pass a highly privileged role to a Lambda function, which can then operate without supervision. But if that Lambda role were created under a permissions boundary, the function, even with the passed role, would be unable to exceed its defined scope. Here, the boundary isn’t just a limit; it’s a fail-safe condition.
This boundary-centric view of IAM requires us to move from a mindset of permission listing to one of permission engineering. Boundaries force us to ask not merely, “What should this role do?”, but more critically, “What must this role never be allowed to do even if compromised or misused downstream?”
In this way, IAM boundaries become more than policy elements. Rather, they become trust instruments, shaping the contract between systems, services, and the engineers who design them.
II. Where Least Privilege Falls Short
Least privilege, in its classical definition, instructs us to grant only the permissions necessary for a user or service to perform its intended function and nothing more. On paper, it reads like a security silver-bullet. In practice, however, it’s a brittle abstraction, dangerously silent about system composition, transitive access, and emergent behaviors.
The problem is not with the principle itself but with its superficial implementation. We construct fine-grained IAM policies, trim unnecessary actions, restrict ARNs, and apply condition keys. Yet we do this in isolation focusing on the shape of individual permissions while ignoring the network of possibilities they enable when composed.
Let us examine a few scenarios where this fragmentation unravels the illusion:
1. Cross-Account Role Assumption with Permissive Trust Policies
An identity in Account A has a tightly scoped policy: it can only assume a single role in Account B. So far, so good. But what if the trust policy on that target role accepts any principal from Account A? The result: any role in Account A, even those unrelated to the task, can now assume the target role. The boundary of control was presumed to lie in the permissions, but the actual breach occurred at the trust level,a layer often forgotten during least privilege audits.
2. Innocuous Lambda Roles as Escalation Vectors
A developer deploys a Lambda function with access only to s3:PutObject in a staging bucket. A textbook case of least privilege. But the function also has environment variable access, which includes credentials for a CI/CD role with broader permissions or worse, iam:PassRole access to a privileged resource. The result is an unmonitored path to privilege escalation, enabled by the connective tissue of AWS services rather than the policy’s text.
3. S3 Bucket Policies That Nullify Scoped Identity Permissions
Suppose a developer’s IAM policy only allows them to write to a single S3 bucket. But that bucket’s resource policy allows access from all IAM roles within the account perhaps for convenience during testing. Now, even roles with no explicit S3 permissions can access the data not because of what they were granted, but because the resource itself invited them in.
Each of these examples shares a common pathology: a permission evaluated in isolation appears safe, but when placed into a larger system of interlocking trust relationships, it becomes dangerous.
This is the blind spot of least privilege, it does not inherently account for composition, for the potential of permission chaining, or for the attack surface created by implicit contracts between services. It operates at the level of policy text, not system behavior.
Security is not merely about what an identity can do it’s about what they can cause to happen, indirectly, conditionally, or transitively. IAM boundaries serve precisely this function: they prevent paths of unintended consequence, even when individual permissions appear benign.
To move beyond least privilege is to accept that denial must be as explicit as allowance, that boundaries must be built not just to guide function, but to limit imagination.
III. IAM Boundaries as Guardrails, Not Permissions
Perhaps the most pervasive misconception in AWS IAM design is the idea that permission boundaries grant access. They do not. In fact, they grant nothing. A permission boundary is not an additive mechanism, it is a subtractive one. Its power lies not in what it allows, but in what it refuses to permit, even when all other layers say yes.
To understand this, one must internalize a subtle but powerful truth: in AWS, effective permissions are the intersection of all policies. And a permission boundary acts as a mathematical filter, truncating the set of allowed actions to the minimum common denominator between what the IAM policy says can be done and what the boundary says should be allowed.
This makes permission boundaries guardrails in the truest architectural sense: they constrain the maximal blast radius of an identity. They are not a blueprint for action; they are a protection against privilege creep.
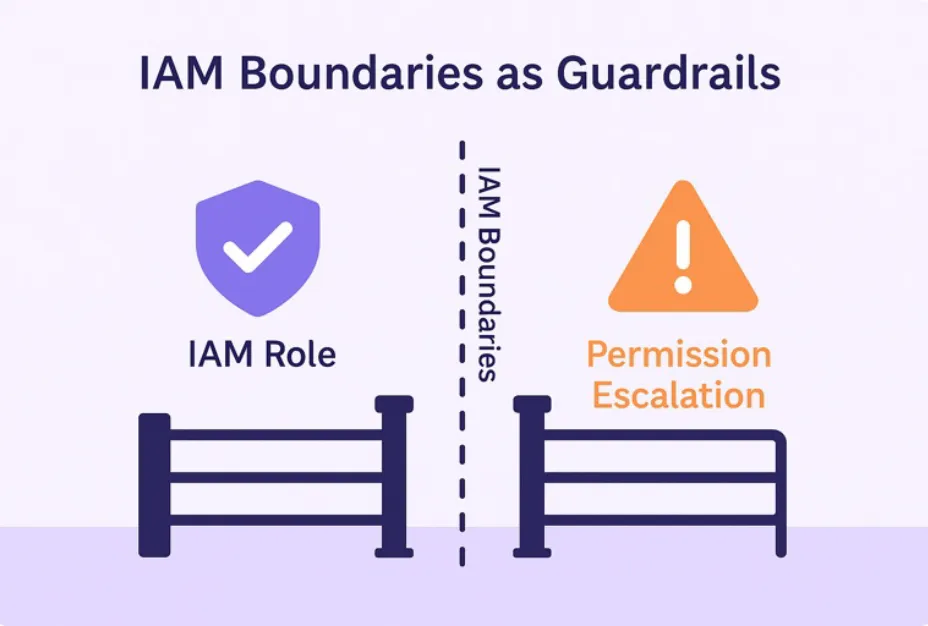
Consider the analogy of a club bouncer. A VIP pass may say you have access to the lounge, but the bouncer has final say and if your name isn’t on the list that night, you’re not getting in. In this metaphor:
- The IAM policy is your VIP pass.
- The permission boundary is the bouncer.
- The trust policy is whether the venue even lets you enter the building.
Now scale that analogy to a cloud environment where hundreds of identities are created dynamically by CI/CD pipelines, by developers using IaC templates, by automation scripts with privilege escalation potential. In such a world, boundaries become the final layer of defense, ensuring that even when a role is overprovisioned, it remains functionally constrained.
Here’s how AWS defines their role:
A permissions boundary is an advanced feature for using a managed policy to set the maximum permissions that an identity-based policy can grant to an IAM role or user. AWS IAM Documentation
Crucially, this means you can allow developers to create IAM roles (e.g., for a new microservice), but you can force them to attach a permissions boundary that prohibits sensitive actions like iam:PassRole, kms:Decrypt, or sts:AssumeRole across trust boundaries. This design pattern is foundational in large organizations, where delegated IAM administration must occur without risking privilege inflation.
Let’s examine a use case:
You permit your CI/CD system to create roles dynamically via Terraform. Normally, this is dangerous, what stops a malicious or misconfigured pipeline from creating a role with AdministratorAccess? But with a permission boundary enforced on the iam:CreateRole call, you can ensure that even if a role is created with an overly permissive policy, it can only exercise permissions defined in the boundary. The role exists, but it is caged.
Furthermore, permission boundaries integrate seamlessly with other IAM constructs:
- With SCPs, they form a nested perimeter: the SCP defines the global organizational ceiling, while the boundary enforces scoped ceilings at the identity level.
- With session policies, they add permanence: even if a temporary session is constrained, the boundary guarantees that constraint persists beyond that session’s lifecycle.
It’s worth emphasizing: permission boundaries are not simply technical levers. They are policy enforcement contracts, encoded in code. They enable distributed IAM governance by letting teams operate independently within securely bounded environments.
In an era where automation is prolific and privilege is often conferred by pipeline rather than person, permission boundaries are not optional.
They are the backbone of IAM security, strong when needed, hidden when not, and designed to prevent failure when other controls break down.
Schedule Free Security ReviewIV. Advanced Patterns in IAM Boundary Enforcement
Once permission boundaries are understood and seen not as just feature toggles but governance primitives, they begin to reveal their strategic value. They are no longer just safeguards, they become enablers of autonomy within constraint, allowing developers, pipelines, and services to move quickly without undermining the structural integrity of your AWS environment.
In this section, we explore advanced patterns where IAM boundaries function as composable units in broader cloud security architectures.
1. Developer Role Creation with Guardrails
In some organizations, developers are empowered to create roles and policies for their applications. This decentralization accelerates delivery, but it can easily spiral into an IAM sprawl nightmare.
The solution? Define a universal permissions boundary, then enforce it on every iam:CreateRole operation. Here’s the pattern:
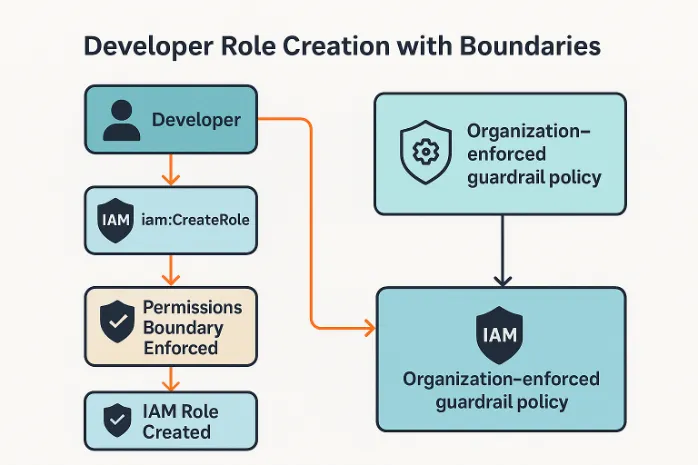
- A permissions boundary policy (e.g.,
DeveloperRoleBoundary) is crafted by security architects to allow only specific services and actions. - An SCP is applied to the developer’s OU, requiring that all created roles must have this boundary attached.
- A CloudFormation or Terraform template enforces this boundary at provisioning time.
The outcome: Developers gain freedom of movement within a defined corridor, unable to grant permissions beyond the boundary, even accidentally.
2. STS Session Policies for Context-Aware Access Reduction
IAM boundaries are static. But real-world privilege should respond to context, time, environment, workload sensitivity.
Enter STS session policies: ephemeral constraints applied during role assumption. When used in tandem with permission boundaries, session policies enable dynamic scoping within a static outer boundary.
Example:
- An incident response engineer assumes a break-glass role.
- Their base role has a wide boundary, allowing for investigative breadth.
- But at time of assumption, an STS session policy is injected, limiting actions to
ec2:Describe*,s3:GetObject, and tagging.
Now the same identity, under different circumstances, inherits a radically different security posture, all without modifying the underlying IAM role.
3. Enforcing Isolation Between Environments Within the Same Account
Traditional IAM architectures assume account-level isolation between dev, staging, and prod. But in modern cost-conscious architectures, teams often colocate environments within the same account, especially during early-stage development.
Here, permission boundaries become surgical instruments:
- Create distinct boundaries for
DevBoundary,StagingBoundary, andProdBoundary, each allowing only the actions appropriate for that tier. - Attach these boundaries to all roles in each environment.
- Implement resource tagging + condition keys (e.g.,
aws:ResourceTag/Environment) within the boundary to ensure that identities only access resources from their own domain.
In this model, even if a role from staging accidentally receives a policy granting s3:DeleteObject on a prod bucket, the permission boundary prevents execution, insulating each environment from policy bleed.
4. IAM Role Escalation Governance in CI/CD Pipelines
Continuous deployment pipelines are often granted elevated privileges, especially if they manage infrastructure or secrets. This creates a toxic pairing: persistent automation + unconstrained privilege.
A resilient pattern:
- Apply a boundary to all pipeline roles (e.g.,
CICDBoundary) that explicitly denies sensitive actions likekms:Decrypt,iam:PassRole, andec2:CreateKeyPair. - Use IAM conditions like
aws:RequestTagto allow temporary elevation,but only when specific tags are present and traceable. - Rotate pipeline roles periodically, and log all deviations using AWS CloudTrail with automated alarms via EventBridge.
Here, permission boundaries serve as non-negotiable ceilings, while pipeline behavior is governed by tags and auditable context.
5. Interleaving SCPs and Boundaries for Layered Control
A common mistake is treating SCPs and permission boundaries as interchangeable. They are not.
- SCPs operate at the AWS Organization level, applying to all principals in an account or OU.
- Boundaries operate at the identity level, applying to specific roles or users.
When used together, they enable nested governance models. For example:
- An SCP prohibits access to
secretsmanager:*in production. - A permission boundary in staging allows read-only access, but disallows creation or deletion.
- The combination ensures that no role, in any condition, can circumvent Secrets Manager controls across environments.
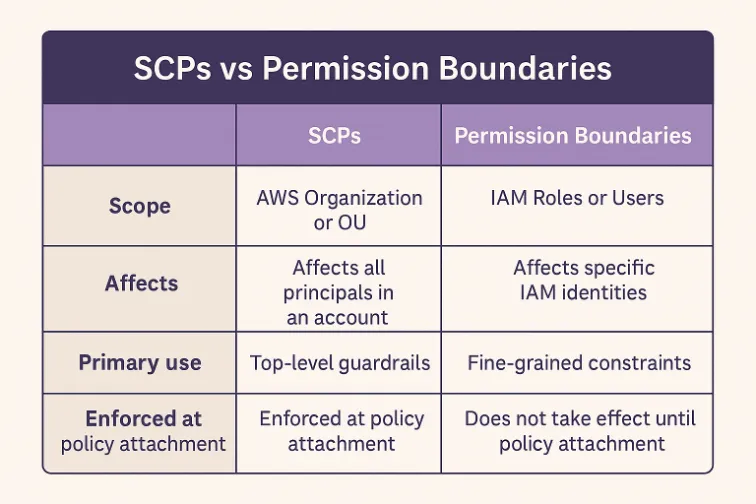
This layering of enforcement levels ensures defense in depth at the policy boundary level, not merely the network or application layer.
These patterns are not exhaustive, but they demonstrate a core principle: IAM boundaries allow you to move from privilege control to privilege architecture. They transform reactive permission management into proactive constraint design, where every role, service, or pipeline is understood not just by what it does, but by what it is categorically prevented from doing.
This shift is vital in modern cloud security. It reframes IAM from a checklist activity into a structural discipline, one that encodes not just access, but the very shape of trust itself.
V. Common Pitfalls and Anti-Patterns & Designing IAM for Intentional Constraint
If permission boundaries represent the skeletal structure of a mature IAM strategy, then it stands to reason that many organizations today are operating with fractured bones and misaligned joints. The complexity of IAM in AWS is not in the writing of policies, it is in the orchestration of those policies across time, context, teams, and trust relationships.
Even when teams understand the basic principles of IAM boundaries, they often fall into predictable traps. Let us diagnose a few of the most anti-patterns that compromise boundary integrity, and then chart a path toward intentional constraint as a design philosophy.
The Illusion of Simulated Safety
The IAM policy simulator is a useful tool, until it becomes your only lens for evaluating effective permissions. Simulators test permissions in isolation, assuming known context and explicit principal-resource interactions. But in production environments, permissions rarely operate in a vacuum. They are invoked by pipelines, chained through SDKs, triggered by EventBridge, or assumed via STS federation. A policy that “looks safe” in the simulator may behave disastrously when wrapped in automation.
Design mandate: Simulate with caution; validate with behavior. Use CloudTrail, Access Analyzer, and real-world request logs to verify boundary behavior under operational conditions.
Misunderstanding the Boundary Hierarchy
It is a common misunderstanding to assume that permission boundaries override or conflict with resource policies or SCPs. In reality, they intersect with them, each acting as an independent constraint. A denial in any one layer is final. Yet many engineers attempt to “correct” access failures by modifying one layer, unaware that another layer is blocking the request.
This leads to policy thrashing, granting broader permissions in the identity policy while missing the real culprit: an overly strict SCP or boundary condition.
Design mandate: Treat IAM like a multi-lens constraint engine. Always evaluate permission failures across all scopes: identity, resource, boundary, session, and organizational level.
Treating SCPs Like Runtime Access Controls
SCPs are often mistaken for runtime enforcement tools, something akin to firewall rules. They are not. SCPs are organizational constraints, preventing even the attachment of permissions, not merely their execution. Over-reliance on SCPs to “stop access” can lead to brittle systems where developers can’t test locally, automation breaks unpredictably, and environment drift accelerates.
Design mandate: Use SCPs as broad perimeter controls. Use permission boundaries to shape fine-grained behavioral limits within that perimeter.
Inline Policy Proliferation and Trust Scope Creep
Inline policies are seductive. They’re easy to attach, visually localized, and appear “harmless” in small doses. But at scale, they become unreviewable, invisible to IAM Access Analyzer, and impossible to enforce uniformly. Worse, they often allow trust policies to widen unchecked, allowing cross-account assumptions, sts:AssumeRole chains, or role-pass actions that create indirect escalation paths.
Design mandate: Codify IAM in infrastructure-as-code. Make boundaries explicit. Design trust policies as contracts, not conveniences.
Designing IAM for Intentional Constraint
Most IAM architectures today are not designed. They are accumulated, layer by layer, ticket by ticket, role by role. This is unsustainable. As the complexity of cloud-native infrastructure grows, IAM must graduate from policy writing to system architecture.
Intentional constraint is the practice of designing IAM not just for access, but for failure.
It begins by asking the opposite of the usual question. Instead of “What must this role do?”, ask:
- What must this role never be able to do?
- What are the unintentional paths it might traverse if chained with others?
- If compromised, how far could it go, and how fast?
This is not merely about restricting permissions. It’s about building IAM systems with predictable blast radius, where each identity is constrained not just by what it knows, but by what the architecture ensures it can never discover.
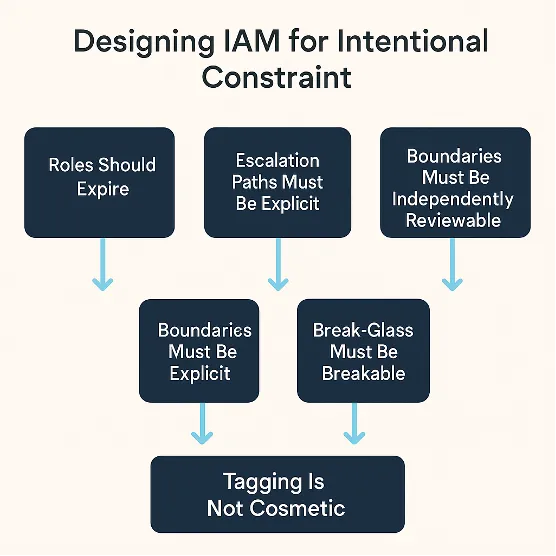
Key principles of intentional constraint include:
Roles Should Expire: Use IAM session durations, token lifetimes, and temporary credentials to make privilege ephemeral. What cannot persist, cannot linger.
Escalation Paths Must Be Explicit: Every role assumption should be traceable and auditable. If Role A can assume Role B, that path should exist for a known, time-bound reason, not as an accident of trust policy defaults.
Boundaries Must Be Independently Reviewable: Design your permission boundaries as artifacts, reviewed like code, versioned like contracts, and tested like logic.
Break-Glass Must Be Breakable: The most privileged roles in your system, incident responders, root-equivalent roles, should be locked behind multiple controls: MFA, session policies, just-in-time elevation. No permission should be God-mode by default.
Tagging Is Not Cosmetic: Use AWS tags as policy gates, tying access to context (
aws:ResourceTag,aws:RequestTag) and ensuring that boundaries respond to environmental signals.
IAM, when properly designed, does not merely prevent bad actors. It will also prevent good intentions from turning into security liabilities. And that is the essence of cloud-native security: not to eliminate risk, but to shape it, contain it, and engineer its failure paths before they are ever tested.
Schedule Free Security ReviewVI. Conclusion: Architecting for Failure, Not Just Access
Today in cloud security, least privilege has long been canonized as the gold standard, the baseline from which all secure architectures emerge. But in practice, it is not a strategy. It is a suggestion. A starting point. A necessary, but hugely insufficient, principle for operating in a dynamic, federated, and composable environment like AWS.
This blog is not a critique of least privilege, but a reframing: IAM security is not about permissions, it is about constraint. About the systematic engineering of what should never happen. About denying not only excessive access, but denying the possibility of emergent privilege, that unpredictable intersection of roles, trust, automation, and accident.
This is why IAM boundaries matter.
They are not there to limit developers. They are there to limit failure, to enforce ceilings on escalation, to bound the blast radius of misconfigurations, to sever privilege paths that could never be anticipated in a static review of JSON policy documents.
In the real world, IAM boundaries function as the “circuit breakers” of access. They trip when assumptions fail. They halt propagation when intentions are outpaced by consequences. They are your final defense against privilege composition, the silent, invisible risk that emerges not from any one policy, but from the way policies stack, bleed, and recurse across time and context.
So if you leave this post with only one question, let it be this:
In your AWS environment, what stops your most privileged roles from becoming more privileged than you intended?
If the answer is, “Nothing except good behavior,” then it’s not an architecture, it’s a wish.
Build IAM like you build infrastructure: with isolation zones, fault domains, guardrails, and constraints. Build it not to grant access, but to constrain the unexpected. Build it to fail safely.
Because in the end, mastery of IAM is not about granting the right permissions.
It is about ensuring that, when things go wrong, and they inevitably will,the system fails in predictable, containable, and recoverable ways.
That is the real boundary.
And it’s yours to define.
