Simplify Cloud Governance with AWS Control Tower
Discover how AWS Control Tower automates multi-account governance with guardrails, logging, and compliance controls.
15 min read
How does one preserve autonomy without descending into anarchy?
This is the paradox at the heart of modern cloud-native architecture. At one end of the spectrum lies the promise of cloud computing: elastic, decentralised, frictionless innovation. On the other hand, the grim inevitability of entropy of environments sprawling out of control, compliance eroding into abstraction, and security devolving into a patchwork of ad hoc conventions.
The allure of AWS, with its near-limitless flexibility, is also its greatest governance liability. Every team, developer, or initiative can spin up environments at will. Every account becomes a sovereign domain, detached from organisational standards and drifting further from any coherent baseline of trust. While this explosion of autonomy may catalyze innovation in the short term, it invariably leaves behind a fragile ecosystem: unscalable, unobservable, and ungovernable.
AWS Control Tower is what we’re discussing today not just as a feature, but as a foundational concept. It’s a governance tool designed to bring order and purpose to cloud growth. It’s AWS’s solution to a key question:
How do you encode institution-wide governance without suffocating innovation at the edge?
Control Tower does not simply automate account creation or enforce service control policies. It does much more; it codifies the organizational memory of what “secure,” “compliant,” and “audit-ready” should mean, then replays that memory every time a new workload is created.
This blog does not seek to rehash what Control Tower is in mechanical terms. Instead, it interrogates why Control Tower had to exist, and why, as cloud adoption matured, enterprises needed a way to govern without centralizing, to restrict without paralyzing, and to orchestrate freedom without defaulting to chaos.
But…, What Is AWS Control Tower?
AWS describes Control Tower as “a managed service that automates the setup of a landing zone for your multi-account AWS environment, based on AWS best practices for security and compliance.” This description is accurate but inadequate. It captures the instrumental nature of Control Tower and what it does but fails to capture the real significance of what it represents.
To grasp Control Tower’s true nature, one must understand it beyond just being another tool in the AWS ecosystem. This is a meta-orchestrator, a higher-order abstraction that composes lower-level primitives into a coherent governance framework. Where individual AWS services expose capabilities, Control Tower encodes intentions. It sets up, establishes, and builds in AWS’s opinions about how cloud environments should be built, secured, and scaled.
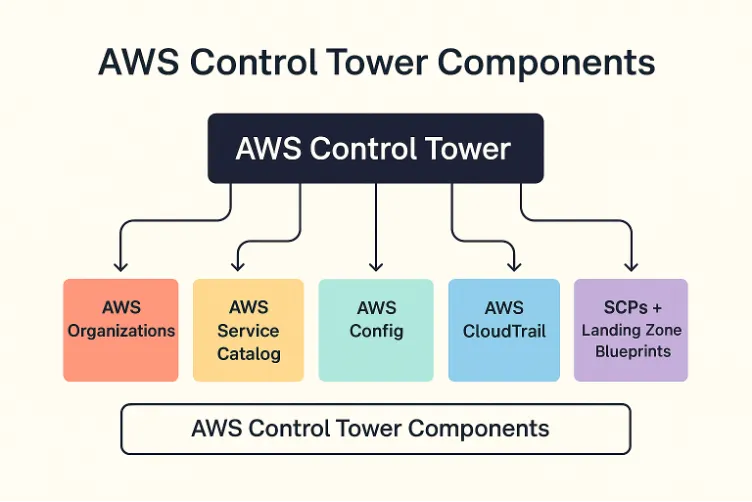
At its core, Control Tower combines multiple services. Each service handles a different part of governance, and Control Tower manages them all from one central place:
- AWS Organizations becomes the substrate of hierarchy and inheritance, providing the foundational topology of accounts and organizational units.
- Service Catalog imposes constraint by curation, allowing only pre-approved, templated resources to be provisioned through self-service.
- AWS Config tracks compliance over time: not just whether a resource is secure, but when it changed from its expected state.
- CloudTrail, SSO, and Service Control Policies (SCPs) contribute to observability, identity governance, and permission ceilings across the federated account structure.
- All of this is scaffolded within a Landing Zone blueprint, a pre-architected baseline environment into which new accounts are launched with inherited controls, configurations, and constraints.
The end product is not just automation. It is the constitution. Control Tower functions as the constitutional law of your AWS federation. Control Tower goes beyond just a rule engine; it is a codified set of foundational principles that govern new cloud actors’ creation, behavior, and rights (i.e., accounts). It enshrines decisions about network topology, logging requirements, IAM boundaries, region restrictions, all made once and then applied everywhere.
Like a constitution, it establishes what is permitted and what is impossible. A new account spun up through Control Tower is not a blank slate. It is born with organizational expectations, a memory of prior failures, and a memory of what compliance has come to mean within that domain.
This is what makes Control Tower truly useful. It does more than just speed up setup or enforce security rules. It builds good architectural decisions directly into how you expand your cloud environment. Instead of checking for problems after they happen, it prevents them from happening in the first place.
And therein lies the deeper question: What does your cloud environment remember?
Control Tower ensures that every new account automatically, consistently, and without relying on human vigilance remembers the organization’s architectural intent.
The Problem It Seeks to Solve: Fragmentation at Scale
In the early stages of cloud adoption, every new AWS account feels like a small victory another team empowered, another project unblocked, another environment unshackled from the latency of procurement or the inertia of centralized IT. But this unlimited freedom creates a problem: the same decentralization that drives innovation also leads to chaos.
Account sprawl is not a failure. It is a symptom of operational success, scale, initiative, and emergent complexity. Yet as organizations multiply their account footprint, they confront a less celebrated reality: Governance does not scale linearly. It fragments.
Unless governed otherwise, each AWS account becomes its own sovereign territory, a snowflake of security posture, network design, logging strategy, and compliance interpretation. In theory, central security teams can provide guidance. In practice, they become bottlenecks or, worse, irrelevant observers to a chaos they can no longer control.
This is the burden of decentralized cloud governance. Every team becomes an island, wielding root-level permissions over infrastructure that implicitly or explicitly interacts with organizational systems of record, customer data, and regulatory obligations. Without shared scaffolding, even the most well-intentioned teams diverge: one enables global S3 access for testing, another forgets to configure CloudTrail, and a third inadvertently disables GuardDuty.
In the spaces between these divergent accounts, Shadow IT flourishes. Infrastructure is spun up outside formal provisioning pipelines. IAM roles are assumed without boundary constraints. Encryption standards are abandoned for convenience. Over time, the distance between policy and practice becomes untenable. What the organization believes it is enforcing drifts apart from what is actually occurring.
This drift is not merely technical. It is existential. In regulated industries, it is a compliance time bomb. In high-growth startups, it is a silent accrual of technical debt. In security-conscious enterprises, it is a blind spot wide enough to conceal a breach.
And so the question emerges, albeit not a technical one, but a philosophical one:
“In a world of infinite cloud resources, who gets to say ‘no’, and how is that authority encoded?”
Traditionally, the answer was found in human processes: provisioning tickets, architecture review boards, and monthly audits. But these were built for a slower world. In cloud-native systems, where infrastructure is provisioned in milliseconds and misconfigurations can go global in seconds, intent must be embedded in automation. Authority must be encoded, not just in policies, but in inheritance, enforcement, and organizational memory systems.
This is the crisis that AWS Control Tower was born to address. This goes well and truly above just account creation. It elevates Governance as a first-class concern, baked into the substrate of multi-account AWS strategy.
The Governance Dialectic: How AWS Control Tower Resolves Tensions
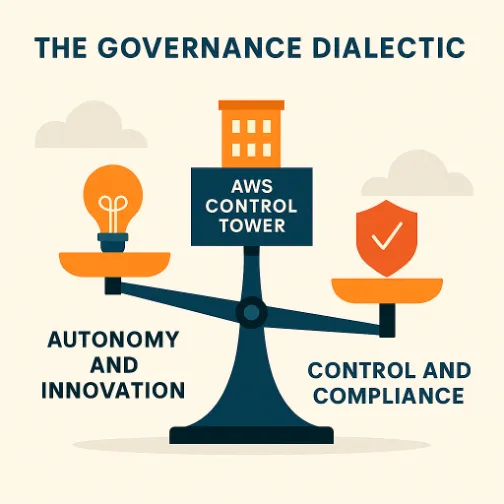
AWS Control Tower balances competing forces: freedom versus control, decentralization versus standardization, speed versus security. Managing these tensions isn’t just about choosing the right tools it’s about how organizations maintain their standards and goals as they grow.
AWS Control Tower is not a product that “solves governance.” It is an opinionated framework that translates governance into automation, distilling abstract principles, security, compliance, and operational integrity into concrete, repeatable outcomes across an ever-expanding surface of AWS accounts. It does this by addressing the main challenges of cloud growth and providing solutions to prevent sprawl. Let’s look at these challenges and how Control Tower solves them.
1. Baseline Enforcement: Architecting the Minimum Viable Trust
One of the core challenges of multi-account environments is ensuring that new accounts are born secure. Left ungoverned, fresh accounts can become vulnerable because they are actively misconfigured or unprotected.
Control Tower addresses this by embedding security baselines into the very act of account creation. Every account spun up through the Account Factory is instantiated with a landing zone blueprint: CloudTrail logging is enabled by default, AWS Config is activated, guardrails are pre-applied, and networking controls are aligned to central patterns. These are enforced defaults, ensuring that no account is provisioned into a governance vacuum.
In this way, the Control Tower’s role transcends that of a controller. It becomes an architectural compiler, automatically and immutably translating high-level governance principles into low-level AWS primitives.
2. Drift Detection: Keeping Reality in Line with Expectations
Compliance in the cloud is not a static achievement. It is a moving target. Even if an account begins securely, it does not remain so indefinitely. Engineers disable logging to troubleshoot. Resources are re-tagged. IAM roles are manually adjusted. Entropy sets in.
Control Tower responds through continuous reconciliation. It integrates AWS Config rules across the landing zone, establishing baseline expectations and then watching for deviation. Every deviation is logged and surfaced as a governance signal, a breach of architectural contract.
This is crucial.
Control Tower does not merely enforce structure; it monitors fidelity to that structure, closing the loop between provision and operation, between desired state and actual state.
3. Guardrail Definition and Enforcement: Institutional Memory in Code
In traditional organizations, institutional knowledge, what “should” be done, resides in documents, internal wikis, and audit PDFs. In Control Tower, that knowledge is transmuted into guardrails: codified SCPs (Service Control Policies) and Config rules that embody best practices, legal requirements, and organizational policy.
These guardrails exist in two forms:
- Mandatory (preventive or detective): Immutable policies that cannot be disabled
- Elective: Best practices that can be enabled or tuned per organizational need
The genius of this model lies in its duality. Guardrails do not take away our ability to make decisions. Instead, they parameterize it. They render governance composable and visible, enabling architects to see it not as a top-down directive, but as a modular control plane.
In this sense, Control Tower becomes a kind of institutional memory made executable. It recommends acceptable architectural behavior, and it encodes it.
4. Account Vending Automation: Controlled Decentralization
Innovation thrives on autonomy. But autonomy without guardrails becomes fragmentation. Control Tower’s Account Factory, backed by AWS Service Catalog, provides a structured solution to this tension.
Teams can request and receive new accounts on demand, but every such request is channelled through a predefined, centrally governed provisioning template. This ensures that:
- Accounts are created within the organizational unit (OU) hierarchy
- Guardrails are attached immediately
- Logging and audit controls are inherited by default
This model does not slow down development. It accelerates it, eliminating friction without eliminating governance. It is autonomy by design, not by neglect.
Real-World Use Case: Enterprise Onboarding and Compliance-by-Design
In early 2025, a mid-sized digital banking firm, Verity Capital (real name changed for confidentiality), engaged us at Avinteli to investigate what had begun as a routine pre-audit concern. The organization had grown rapidly, launching three new service divisions across payments, lending, and asset management, each with its autonomous development team. While AWS adoption had been early and enthusiastic, cloud governance had lagged behind. What started as giving developers more freedom had turned into operational chaos.
Every team operated within its own AWS account, each bearing its own flavor of SCPs, IAM trust relationships, and logging configurations. There were no shared patterns, only ad hoc practices, and what the firm referred to as “policy culture” was, in practice, a collection of internal wiki pages and Slack threads. The technical debt extended well beyond application code; it eroded trust across the infrastructure fabric.
We were brought in ahead of Verity’s SOC 2 Type II compliance cycle, and what we discovered was not merely misconfiguration. We found a profound breakdown in governance continuity, akin to institutional amnesia. No one could say, with certainty, which controls were enforced across accounts. IAM roles proliferated with inconsistent naming conventions. Some accounts had CloudTrail enabled, others did not. Resource tagging was informal and non-standard. Determining which accounts existed required cross-referencing spreadsheets, billing reports, and developer memory.
To reassert architectural cohesion, we led the strategic rollout of AWS Control Tower and initiated a foundational realignment of Verity’s cloud governance philosophy.
We began by working closely with their internal cloud team to establish a Landing Zone architecture tailored to their compliance and operational needs. Every new account provisioned through Account Factory now inherits a defined governance baseline: SCPs aligned to environment sensitivity (dev, staging, prod), centralized logging via CloudTrail, preventive and detective controls through AWS Config, and IAM boundaries enforced through standardized permission sets.
Verity’s cloud ecosystem was transformed, what emerged was not just automation, but the institutionalization of constraint as code. We didn’t merely implement guardrails, we canonized them. Policies became reproducible infrastructure, not reactive defenses. Development teams gained autonomy, but within clearly defined corridors of compliance, where innovation could flourish without the latent risk of regulatory erosion.
Previously, onboarding a new team meant navigating one-off scripts, tribal knowledge, and manual tagging. Post-Control Tower, onboarding became productized: a team requested an account, and Control Tower delivered a fully governed environment, guardrails pre-enforced, audit readiness embedded, and misconfiguration structurally excluded.
The result? Verity’s GRC posture improved dramatically. Audits once triggered weeks of retroactive evidence gathering, but now, thanks to Config-based compliance detection baked into every account, they require little more than presenting policy blueprints and verifying drift status.
In our post-project review, we saw that compliance was no longer something that happened occasionally; it had become constant.
As we often tell our clients at Avinteli:
“Governance doesn’t scale when it’s enforced through documents. It scales when it’s enforced through architecture.”
That is precisely what Control Tower enabled, a shift from governance as documentation to governance as infrastructure: composable, reproducible, and dependable.
Extensibility and Misconception: Control Tower Beyond the Console
One of the more persistent criticisms against AWS Control Tower is its supposed inflexibility, an opinionated service, wrapped in a friendly console, that resists deep customization. But such critiques often mistake the default for the definitive.
Control Tower doesn’t prevent customization; it merely demands intentionality. Through features like Account Factory Customization, Control Tower works with Infrastructure-as-Code tools like Terraform. At Avinteli, we’ve embedded Control Tower into account creation workflows. New accounts are provisioned declaratively, with guardrails, baselines, and identity mappings codified in pull requests rather than built through point-and-click wizards.
The system permits a rich spectrum of augmentation:
- Custom AWS Config Rules
- Bespoke SCPs
- Lambda-backed remediation
- Event-driven policy evaluations
The question, then, is not whether Control Tower supports extensibility but whether organizations are willing to treat Governance as code rather than as an operational afterthought.
But even as teams adopt this approach, some common problems persist:
- Misunderstanding guardrails as suggestions rather than enforced controls leads to false assumptions about the blast radius of misconfigured identities.
- Overreliance on Control Tower defaults breeds a false sense of security, especially when organization-level SCPs evolve independently or when Config rules are disabled to reduce perceived noise.
- Treating Control Tower as a one-time scaffold set and forgotten ignores the fact that governance, like infrastructure, is a living system. The cost of drift is not merely misalignment; it is latent exposure.
- Finally, assuming Control Tower will solve everything “out of the box ” is a categorical error. It is not a silver bullet. It is a control plane, a scaffolding for orchestrated governance, not the sum total of your security model.
So, the more compelling question is not “Is Control Tower flexible enough?”, but rather:
Can your organization evolve its governance posture fast enough to match the rate at which cloud complexity compounds?
Control Tower isn’t the Kubernetes of AWS yet, but it could be. The potential is there for it to become a foundational platform for organizational governance at scale.
If we build for it.
Conclusion: Control Tower as a Metaphor for Strategic Cloud Maturity
At its surface, AWS Control Tower appears to be a managed service, a provisioning framework, an account scaffolding, and a governance overlay. But such a description fails to grasp its deeper proposition. Control Tower is not simply a convenience layer; it is an architectural expression of intent in an environment otherwise shaped by entropy.
At Avinteli, we see Control Tower as a tool that doesn’t just enforce rules but builds them into the system itself. Its real power isn’t just in the guardrails it creates, but in how it defines the balance between giving developers freedom and maintaining organizational control.
In this way, Control Tower functions as a kind of constitutional substrate: it declares not just who may act but under what conditions such actions are rendered legitimate, auditable, and recoverable. It institutionalizes memory, codifies guardrails as first-class citizens, and transforms policy sprawl into a repeatable, inspectable structure.
Ultimately, this is what “strategic cloud maturity” means: not faster setup or fewer controls, but consistency; a governance system that grows with the organization, one step at a time.
So if your cloud estate were a sovereign entity, fragmented, distributed, and in motion, what would govern its rights, responsibilities, and limits?
What constitution defines its behaviour when everything else fails?
Control Tower might be your first draft.
Stay tuned for our upcoming blog detailing how to set up a baseline Control Tower implementation.
