How to Detect Security Threats with AWS Trusted Advisor
Learn how AWS Trusted Advisor's security checks help you proactively identify vulnerabilities and compliance gaps before costly incidents.

7 min read
Security misconfigurations are among the leading causes of cloud breaches, with organizations often unaware of vulnerabilities hiding in plain sight within their AWS environments. Fortunately, AWS provides a powerful built-in tool to help identify these issues before they become costly incidents.
Before we get started, I’m going to give a brief description of what
Trusted Advisor
is, and then we’ll jump into how we can use Trusted Advisor to detect security threats in our AWS accounts.
AWS Trusted Advisor is a tool that provides recommendations to help you follow AWS best practices across five key categories: cost optimization, performance, security, fault tolerance, and service limits. It continuously analyzes your AWS environment and compares your resource configurations against established best practices to identify opportunities for improvement. We will be looking at the built-in security checks that are part of Trusted Advisor in this post.
INFO
One thing to note is that Trusted Advisor offers different levels of checks depending on your AWS Support plan. In this blog post, we will be focusing on the checks that are included with the free support plan that comes with all AWS accounts.
Now that we have a high-level understanding of what the Trusted Advisor service is, let’s jump into using it to perform security checks in our environment.
Trusted Advisor Service
Now let’s start by navigating to the Trusted Advisor service by searching for it in the search bar. See figure 1.0 below.  Figure 1.0
Figure 1.0
Once you have navigated to the Trusted Advisor service, you should see a screen similar to the one below in Figure 1.1. Based on the AWS resources that you have deployed in your account, your screen will look different than the one shown in Figure 1.1.
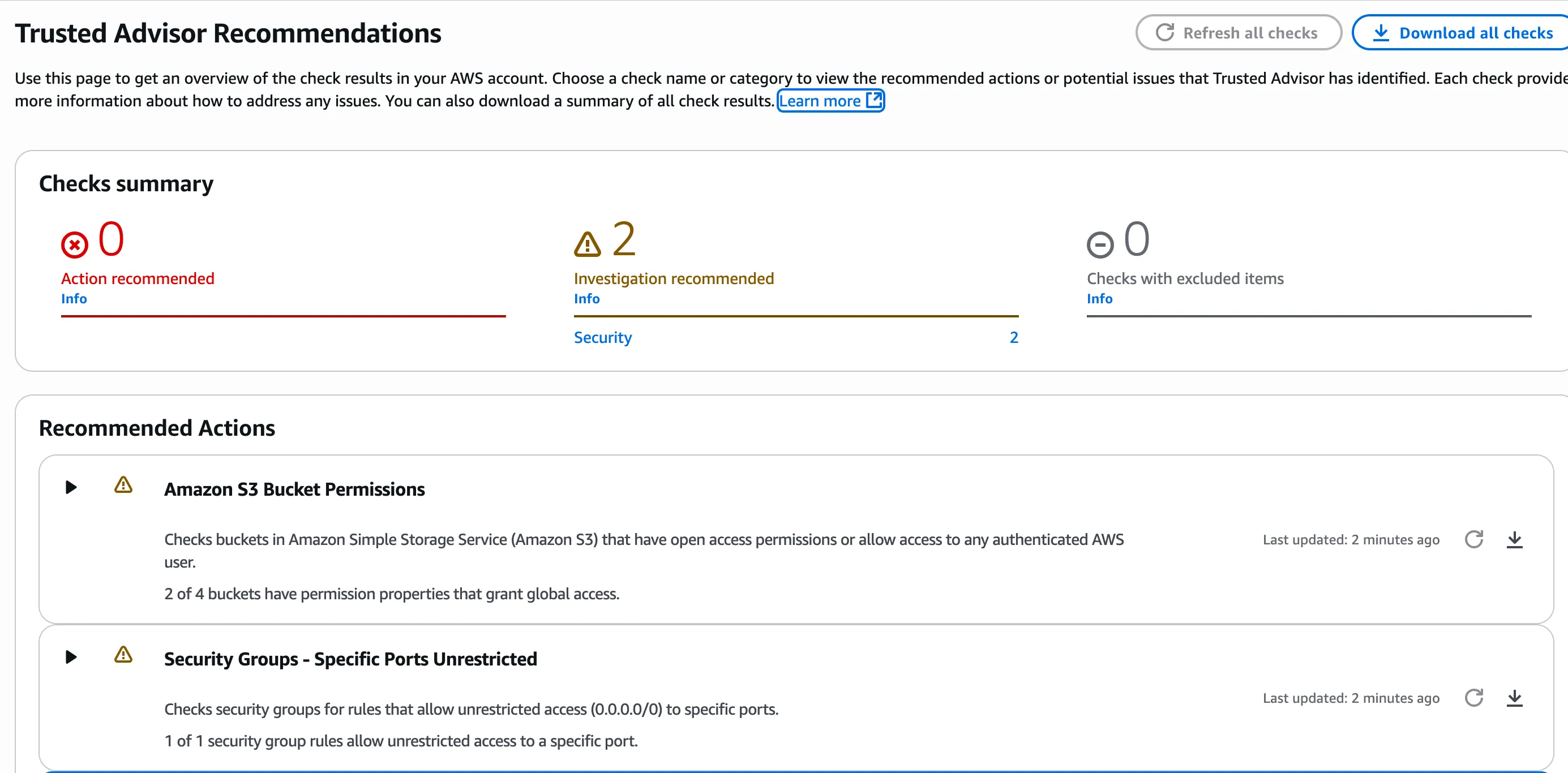 Figure 1.1
Figure 1.1
Trusted Advisor - Checks Summary
In figure 1.1 above you can see in the Checks Summary section that Trusted Advisor gives you different color-coded recommendation levels which are Red, Yellow, and Gray.
Below you can find an explanation of each recommendation type.
(Red) Action recommended – Trusted Advisor recommends an action for the check. For example, a check that detects a security issue for your IAM resources might recommend urgent steps.
(Yellow) Investigation recommended – Trusted Advisor detects a possible issue for the check. For example, a check that reaches a quota for a resource might recommend ways to delete unused resources.
(Gray) Checks with excluded items - The number of checks that have excluded items, such as resources that you want a check to ignore. For example, this might be an Amazon EC2 instance that you don’t want the check to evaluate.
We can see in our Trusted Advisor screen in Figure 1.1 that I have two yellow recommendations which I should investigate further. Let’s dive into what these two security findings are and how to address them.
Trusted Advisor Security Checks
In figure 1.1 we can see we have one Recommended Action related to Amazon S3 permissions and one related to Security Groups.
Let’s first take a look at the Amazon S3 bucket permission issue.
Amazon S3 Bucket Permissions
I have expanded the Amazon S3 Bucket Permissions recommended action in figure 2.0 below and received information related to the alert criteria, recommended action to take, and additional resources. We can use this information to help us resolve this Trusted Advisor alert.
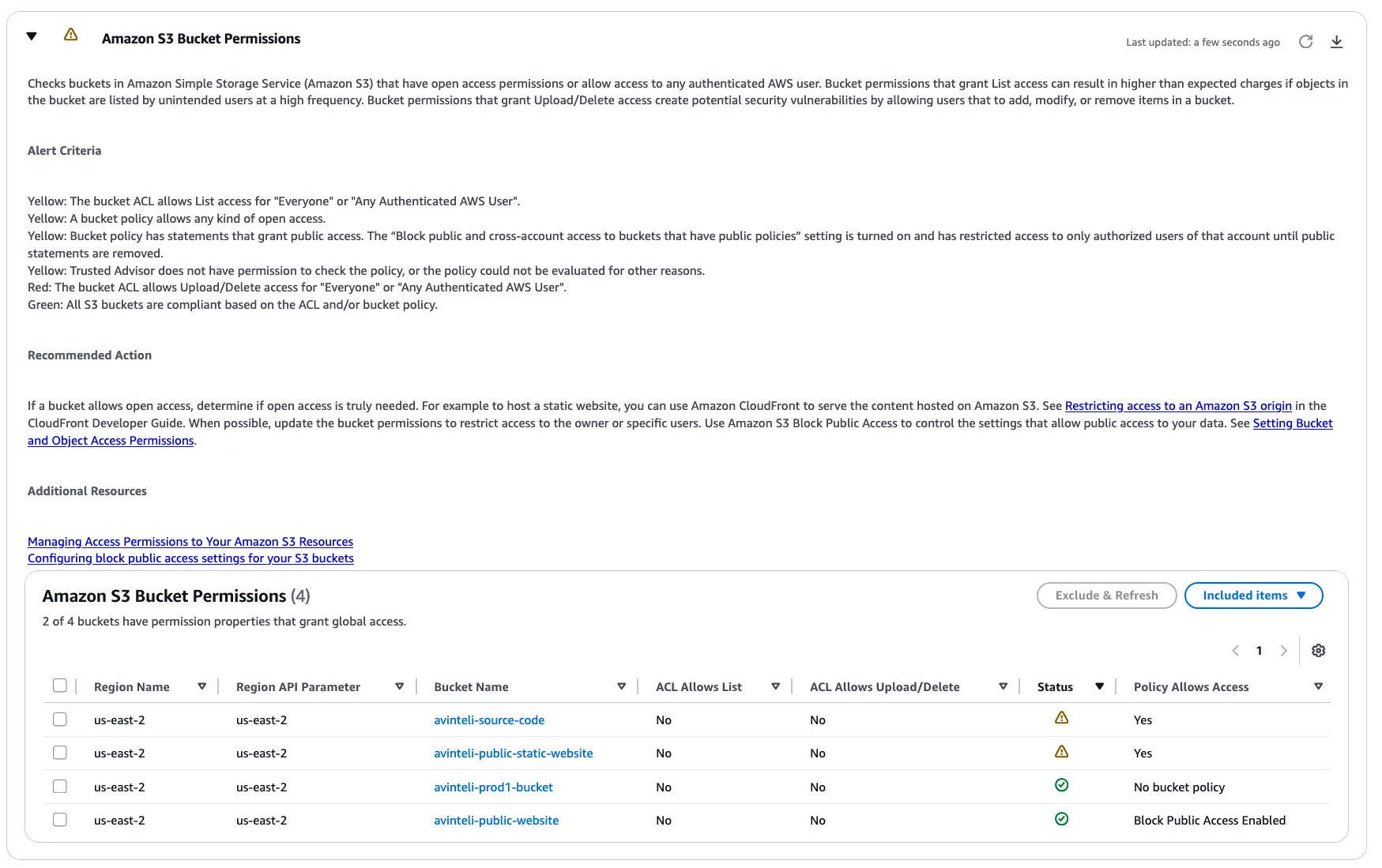 Figure 2.0
Figure 2.0
Now let’s look into what AWS resources are being flagged by Trusted Advisor as it relates to S3. In Figure 2.1 below we can see there are two S3 buckets that allow public read access, which are causing this alert in Trusted Advisor.
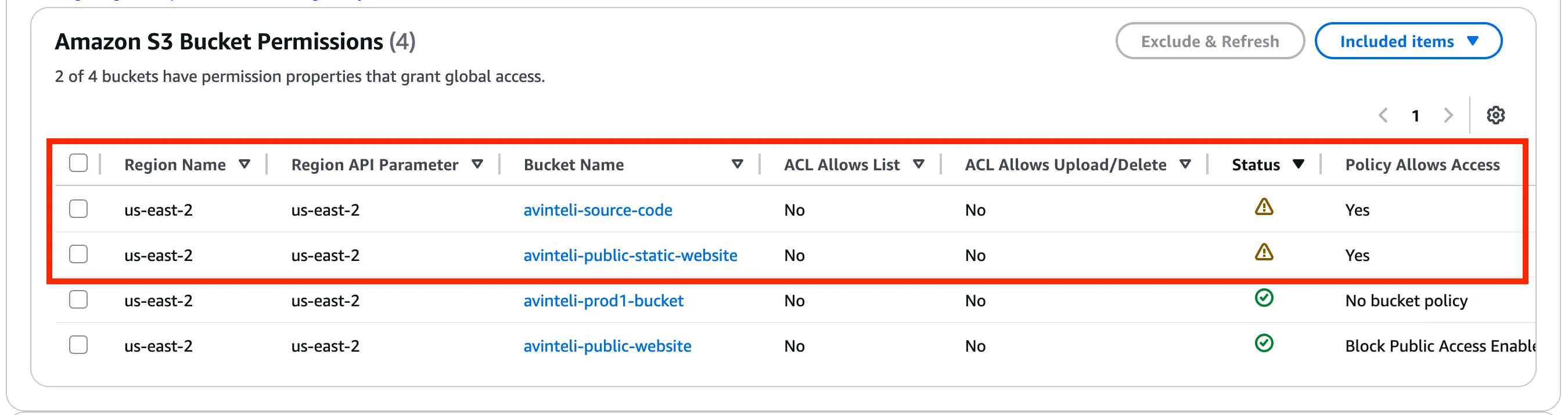 Figure 2.1
Figure 2.1
Note: For buckets that should not allow public access, you should always to block public read/write access unless the S3 bucket is hosting public resources such as static websites.
Buckets that are meant to be publicly accessible, you can click the checkbox next to the bucket name in Trusted Advisor and then click the Exclude & Refresh button, as shown in Figure 2.2 below. Following these steps will prevent the bucket from being flagged in the next Trusted Advisor check.
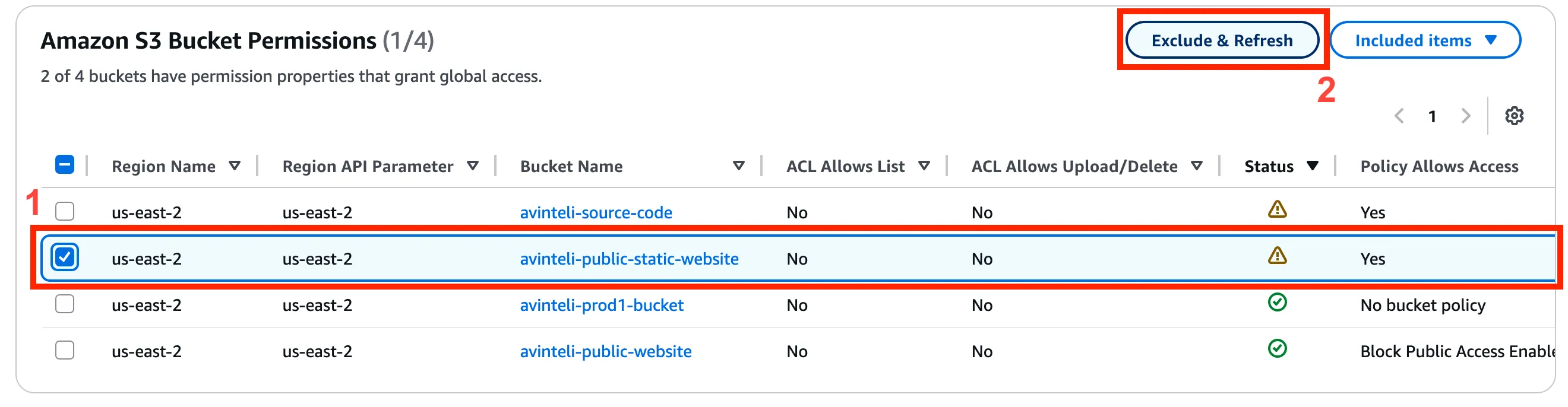 Figure 2.2
Figure 2.2
Next let’s look into the Security Group that was flagged by Trusted Advisor.
Security Groups - Specific Ports Unrestricted
When I expand the Trusted Advisor check for the Security Groups - Specific Ports Unrestricted alert in figure 3.0 below we can see information related to the alert criteria, recommended action to take, and additional resources. We will use this information to guide in fixing this security issue.
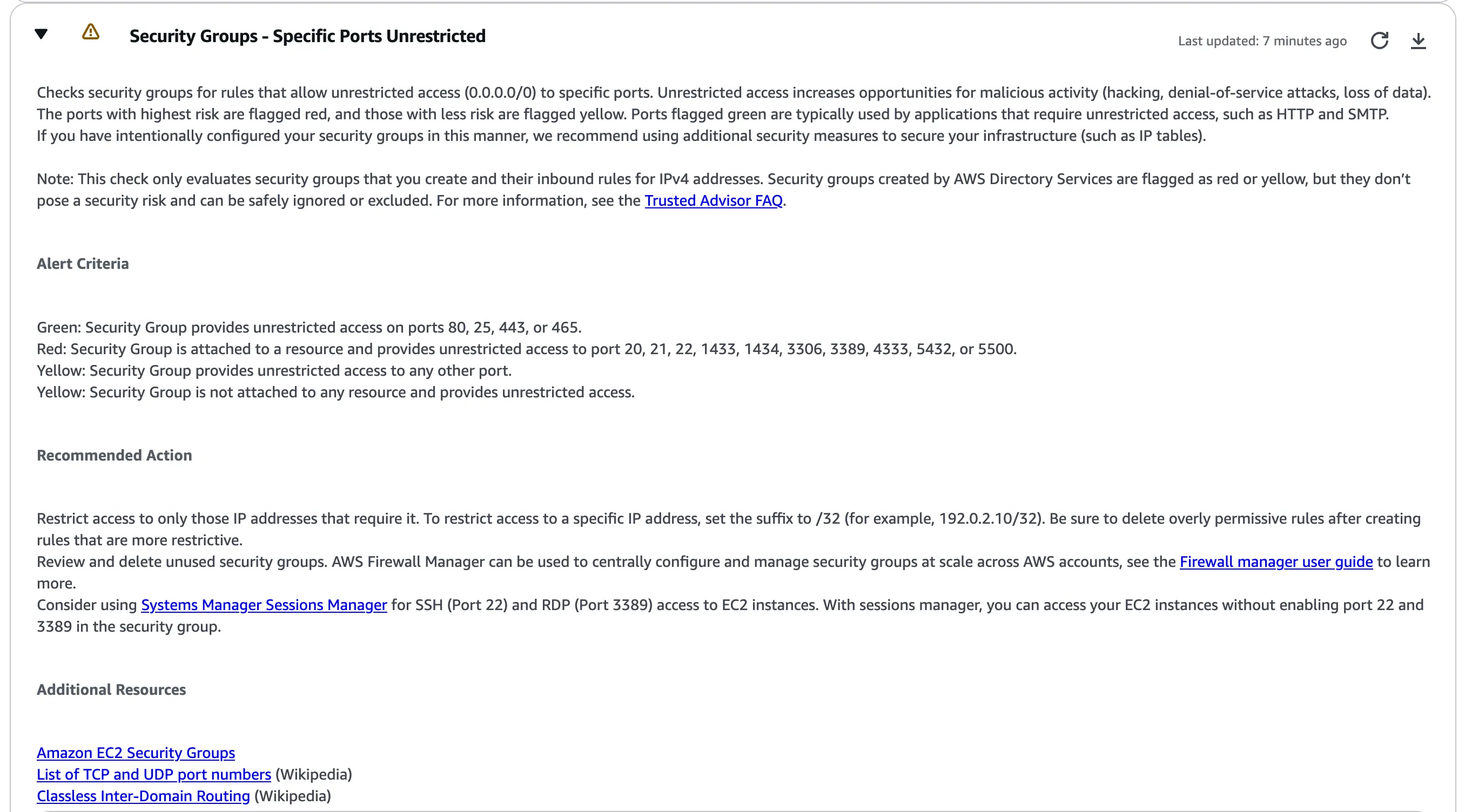 Figure 3.0
Figure 3.0
In Figure 3.1 below we can see this alert relates to a security group that has unrestricted access from any IP address on any port. Having a security group that allows traffic from any IP address to any port is a significant security risk. For any Trusted Advisor finding related to unrestricted port access, it is recommended to limit which ports can receive inbound traffic via the security group.
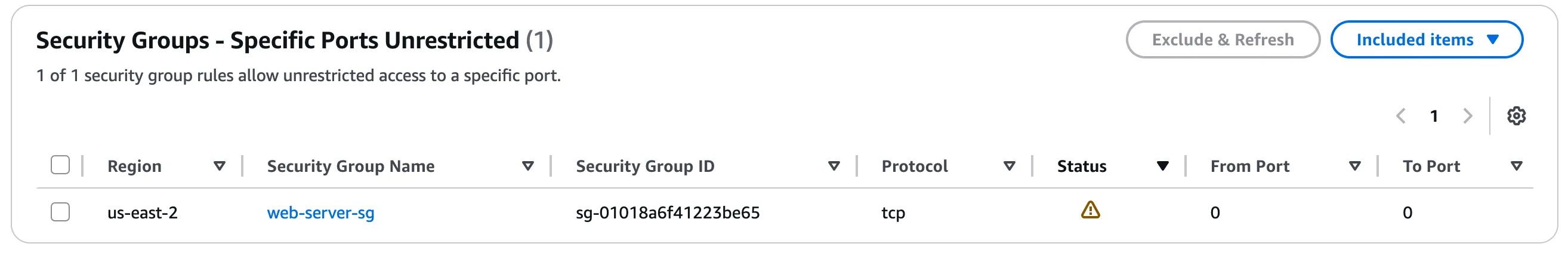 Figure 3.1
Figure 3.1
To fix this security issue, you can click the name of the security group to navigate to the security group in the AWS Console. So, for us we would click on web-server-sg in figure 3.1 in order to navigate to the security group to limit traffic to specific inbound ports. Since the security group here appears to be for a web server, we would allow inbound traffic only on port 80 (HTTP) and 443 (HTTPS).
Note: You can also use the Recommended Action steps outlined in figure 3.0 if you are unsure how to resolve this security finding on your own.
TIP
Ensure you have an AWS Business Support plan when running production workloads.
From the Field
This leads me to share a critical observation from my professional experience.
During my tenure as a Senior Security Solutions Architect at Amazon Web Services, I conducted security assessments for many Fortune 500 companies and consistently identified a significant gap in many environments. Many organizations running mission-critical production workloads did not have the appropriate support plan, which limited the types of checks available to them in Trusted Advisor. Without proper support coverage, these enterprises were significantly limiting their visibility into AWS’s built-in security intelligence provided by the Trusted Advisor service.
The financial and reputational costs of security incidents far outweigh the investment in proper support coverage. I strongly recommend securing at least an AWS Business Support plan before deploying any production workloads. This isn’t just a best practice; it’s essential to ensure you’re leveraging AWS’s full security monitoring capabilities to protect your business-critical assets.
Schedule Free Security Review
Conclusion
AWS Trusted Advisor serves as a valuable first line of defense for identifying common security misconfigurations in your AWS environment. By leveraging its built-in security checks, you can proactively address issues like overly permissive S3 bucket policies and unrestricted security group rules before they become serious vulnerabilities. The color-coded recommendation system makes it easy to prioritize which findings require immediate attention versus those that need investigation. Regular monitoring of these recommendations should be part of your ongoing cloud security strategy.
While the free tier of Trusted Advisor provides essential security checks, remember that comprehensive cloud security requires a multi-layered approach. Trusted Advisor’s security checks are just one component of a broader security framework that should include proper IAM policies, network segmentation, monitoring, and incident response procedures. For production environments, consider upgrading to a Business Support plan to access additional security checks and more detailed recommendations that can help you maintain a robust security posture across your AWS infrastructure.
Other Blogs
Complete Guide to Detecting Public Buckets with IAM Access Analyzer for S3
- About Author
Sheldon Sides
LinkedInSheldon is Founder and Chief Solutions Architect at Avinteli. Before founding Avinteli, he led Global Security and Compliance at Amazon Web Services (AWS) for Public Sector Partners and Global ISV Partners. Prior to his leadership role, he served as a Senior Security Solutions Architect at AWS, where he conducted comprehensive security assessments and guided Fortune 500 companies through complex, enterprise-scale AWS cloud implementations. His deep cloud security expertise and hands-on assessment experience help organizations identify critical vulnerabilities, close security gaps, accelerate their secure cloud adoption, and design and develop cloud-native solutions.
