Secure Your AWS Root Account - Step-by-Step Login Monitoring Guide
Automate AWS root account login detection with real-time alerts using CloudTrail, EventBridge, and SNS.
7 min read
Your AWS root account is the most powerful credentials in your entire cloud infrastructure. Understanding why this account requires extraordinary protection is critical to maintaining your organization’s security.
Think of your AWS root account as the master key to your entire cloud environment. This account has ultimate control. It can bypass any security rules for other users, wipe out your entire cloud configuration, change your billing details, and even shut down your AWS account. If an attacker manages to log in with your root credentials, it’s one of the worst things that can happen to your AWS setup.
Why You Should keep an eye on AWS Root Account Logins
Think of the root account in AWS as the ultimate master key. It sits above all the usual rules and restrictions set up by IAM (Identity and Access Management). This means the root account can do pretty much anything, including:
- Creating or deleting IAM users and roles.
- Shutting down your entire AWS setup or deleting all your resources.
- Looking at your billing and payment information.
- Turning off important security settings.
Because of this immense power, AWS suggests you only use the root account to set up your account initially. After that, they recommend locking it down. But let’s be honest: People don’t always remember this advice. It’s quite common for root account logins to still happen in production environments, often without anyone even noticing. That’s why extra caution should be taken. This blog post will walk you through how to set up real-time alerts for root account logins. Stay tuned as we break it down step by step.
Prerequisites for This Guide
Before you dive into the steps, make sure: You have an AWS account with appropriate permissions to:
- Create a CloudTrail trail
- Configure Amazon EventBridge rules
- Create and manage SNS topics and subscriptions and lastly
- You have a valid email address to receive alert notifications.
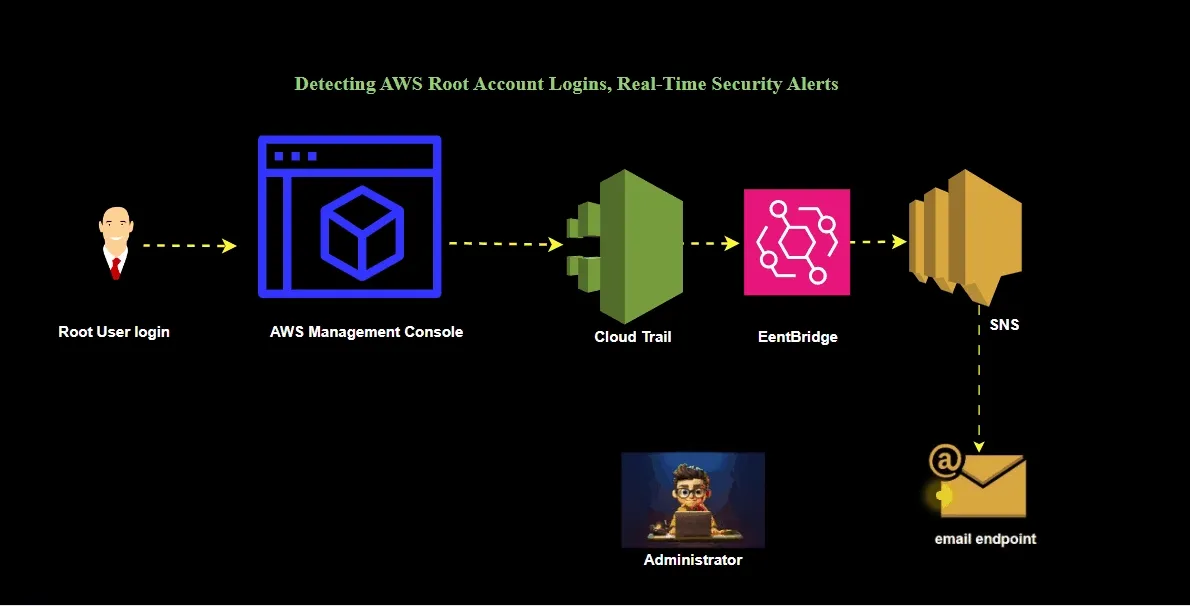
Step-by-Step Guide: Setup Root Login Alerting leveraging EventBridge and SNS
Step 1: Enable AWS CloudTrail (If Not Already Enabled)
Log in to the AWS Management Console in your preferred region. In the search bar at the top, type CloudTrail, then select it under Services.
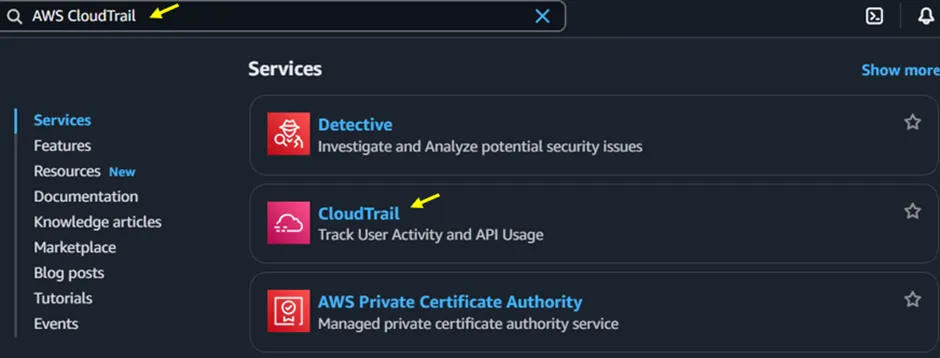
Figure 1
In the CloudTrail console, click on the Create a trail to proceed.
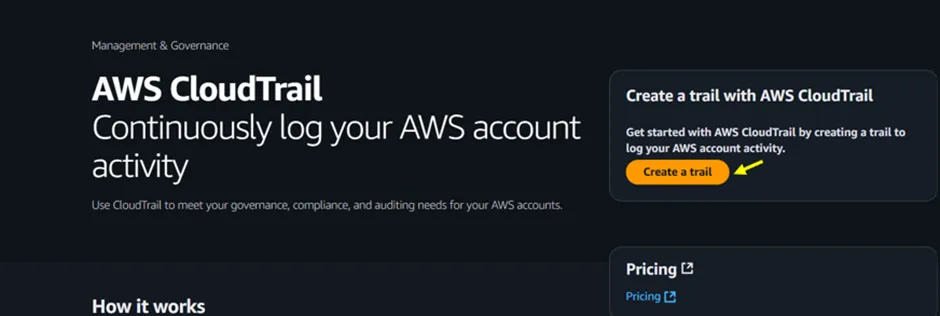
Figure 1.2
Next, you will be directed to the Trail creation wizard in Figure 3 below. Under Trail name, enter a descriptive name for your trail. For the Storage location, you can either:
- Select an existing S3 bucket
- Or choose “Create new S3 bucket” (recommended for clean setup, as shown below).
You may enable log file encryption using an AWS KMS key. However, for this guide, we will proceed without enabling encryption.
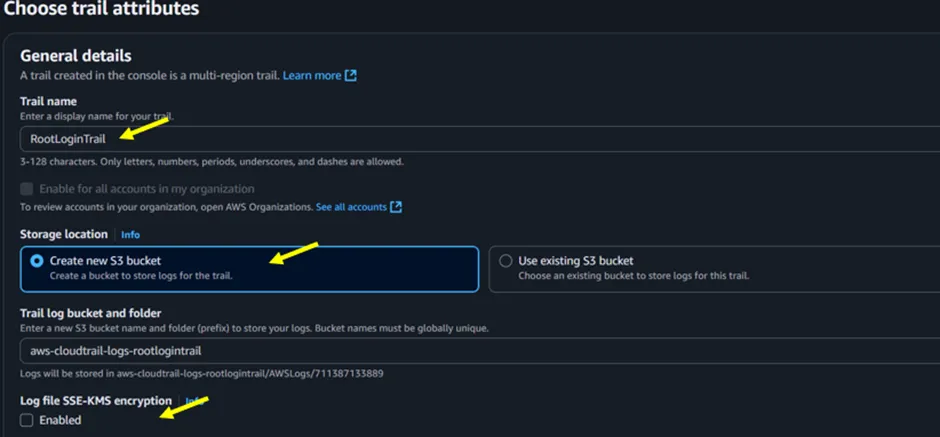
Figure 1.3
Again, we will disable log file validation and CloudWatch Logs integration. Scroll down to the bottom of the page, then click Next.
 Figure 1.4
Figure 1.4
In the Choose log events section, select Management events (Figure 1.5) to ensure that key account activities, including root logins, are captured.
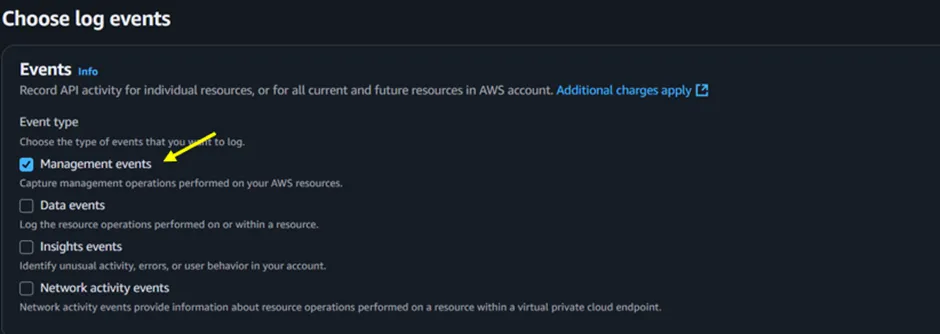 Figure 1.5
Figure 1.5
For API activity, select Read and Write to capture both types of operations for management events, then click Next.
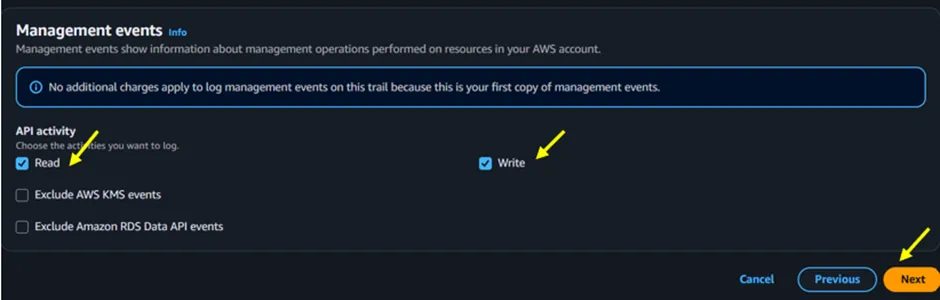 Figure 1.6
Figure 1.6
The next page is the review screen. Carefully review all your configurations, and if everything looks correct, click Create Trail to complete the setup.
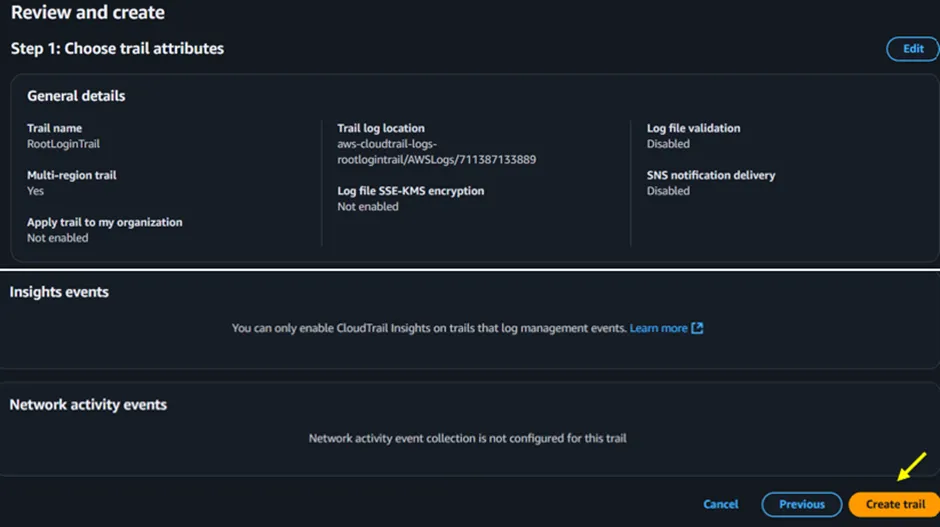 Figure 1.7
Figure 1.7
Our trail has now been created as shown below, and its status is logging.
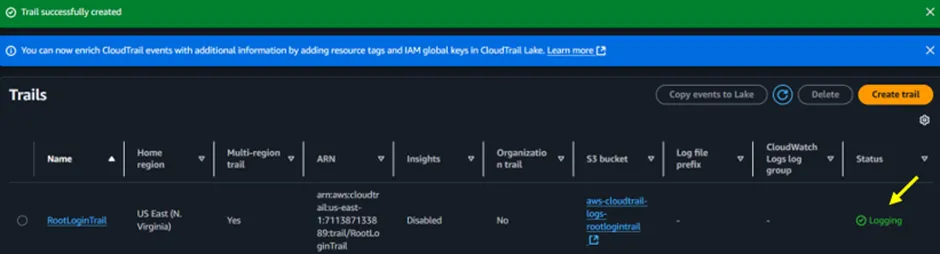 Figure 1.8
Figure 1.8
Step 2: Create an SNS Topic for Alerts
In the search console type in SNS, then select it under services.
 Figure 2
Figure 2
In the left sidebar, click on Topics, then click Create topic.
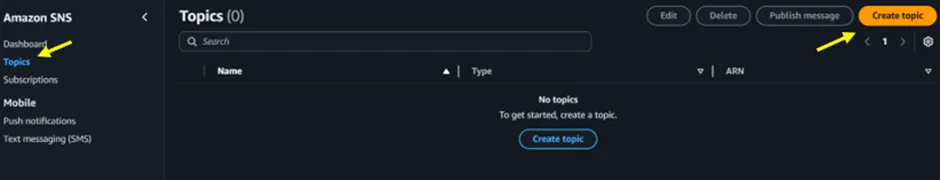 Figure 2.1
Figure 2.1
In the create topic screen (Figure 2.2), under details, select Standard, then under name, give your topic a suitable name.
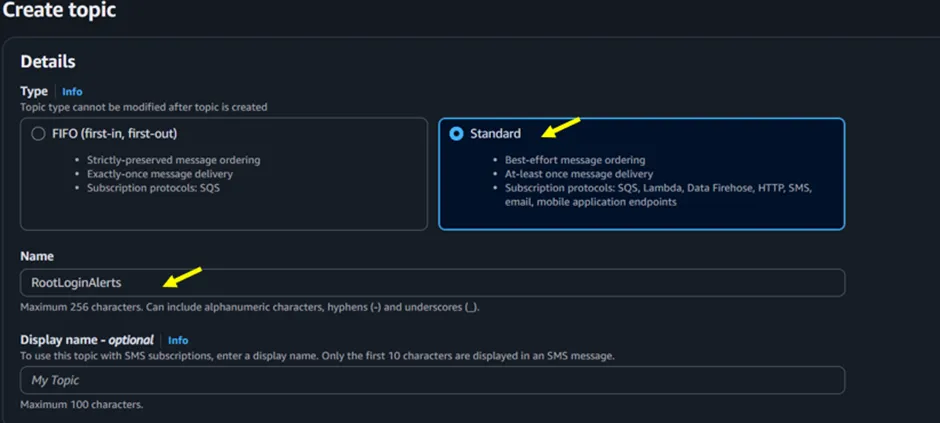 Figure 2.2
Figure 2.2
Those are the only settings we need. Scroll down and click on Create topic.
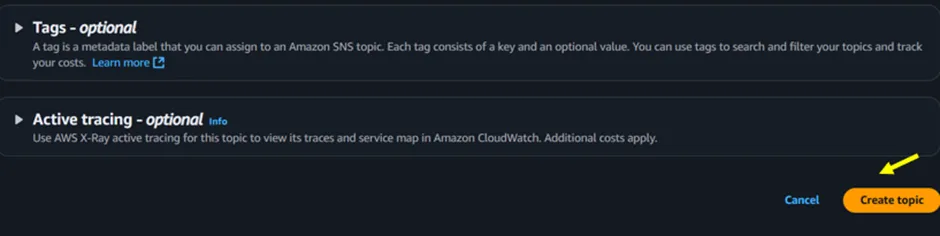 Figure 2.3
Figure 2.3
The SNS topic has been created.
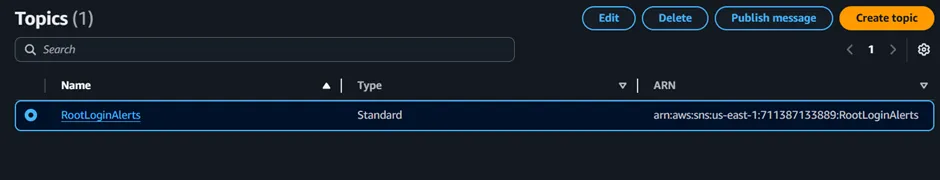 Figure 2.4
Figure 2.4
After creating the SNS Topic, the next step is to create a subscription for it. Click on the topic you created, then scroll down to the subscription tab and click on Create Subscription.
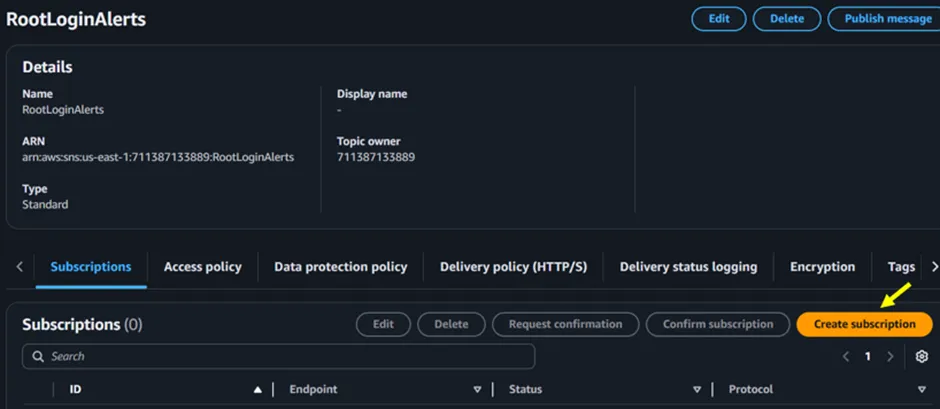 Figure 2.5
Figure 2.5
In the Create subscription screen, for the Protocol, select Email from the dropdown. Then, for Endpoint, input the email address to which you wish to receive the notification.
Next, scroll down and click on Create subscription. The SNS Subscription will now notify you when the root account logs in.
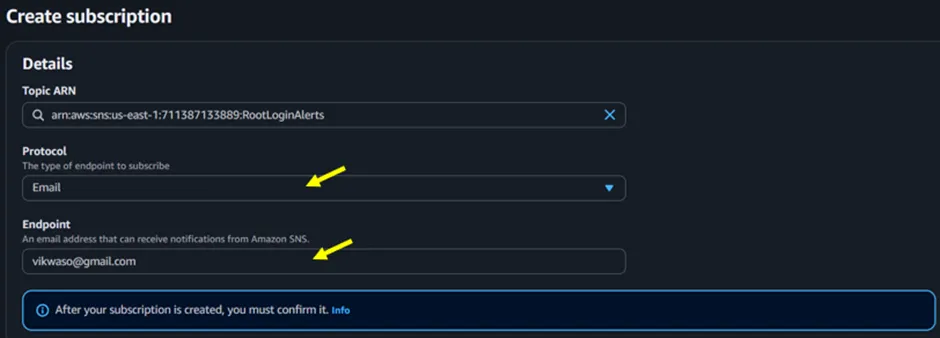 Figure 2.6
Figure 2.6
 Figure 2.7
Figure 2.7
As can be seen below, our Email has been created, but its status is pending confirmation. Go to your email inbox and confirm your SNS subscription.
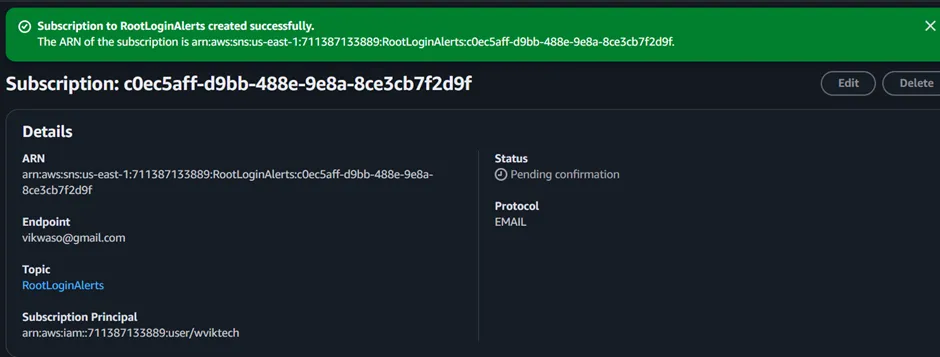 Figure 2.8
Figure 2.8
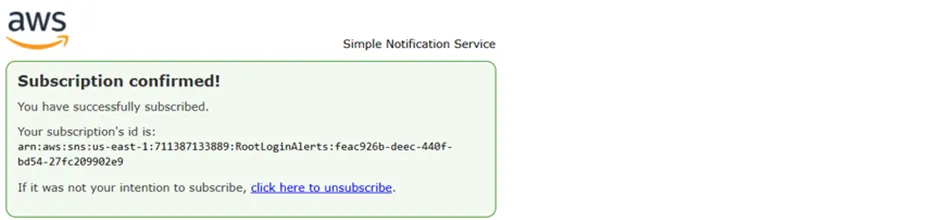 Figure 2.9
Figure 2.9
As seen above in Figure 2.9, our subscription and its status are now confirmed.
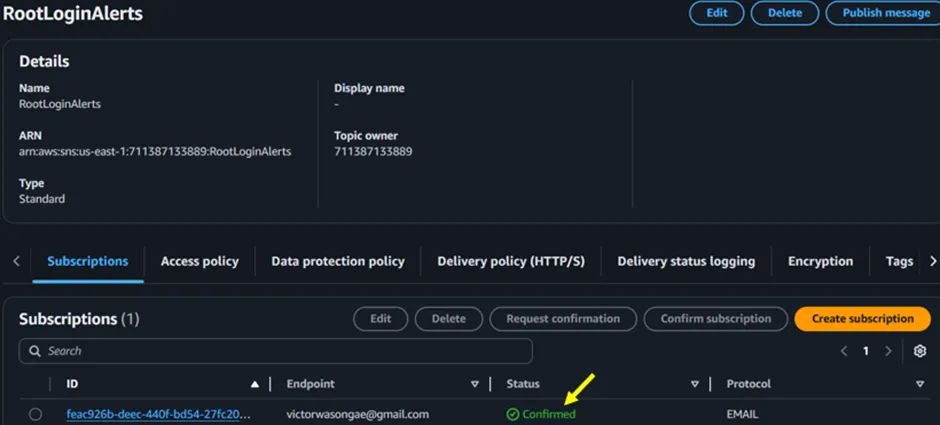 Figure 2.9.1
Figure 2.9.1
Step 3: Create an EventBridge Rule to Detect Root Login Events
Open the Amazon EventBridge console.
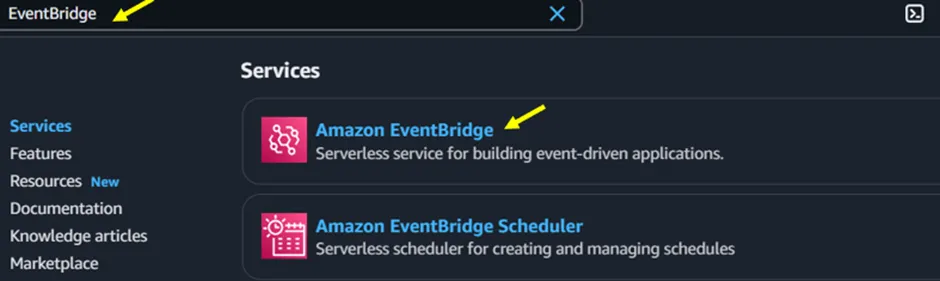 Figure 3
Figure 3
Click the Create Rule button seen in Figure 3.1.
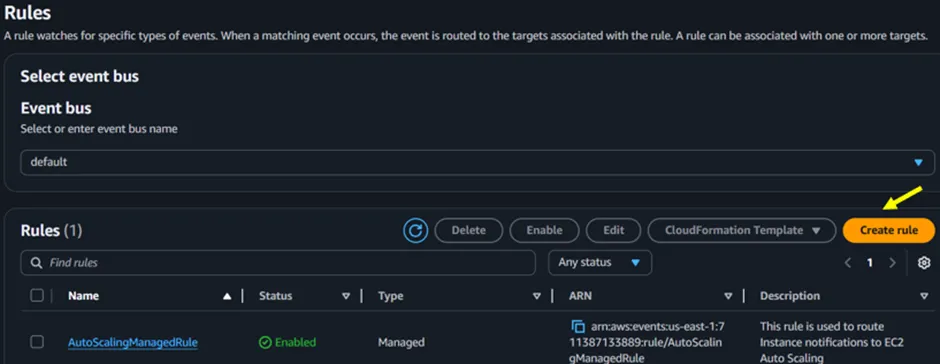 Figure 3.1
Figure 3.1
Under the Define Rules details, give your Rule a preferred name, leave Event Bus the default, and click on Next. For the rule type, select Rule with an event pattern.
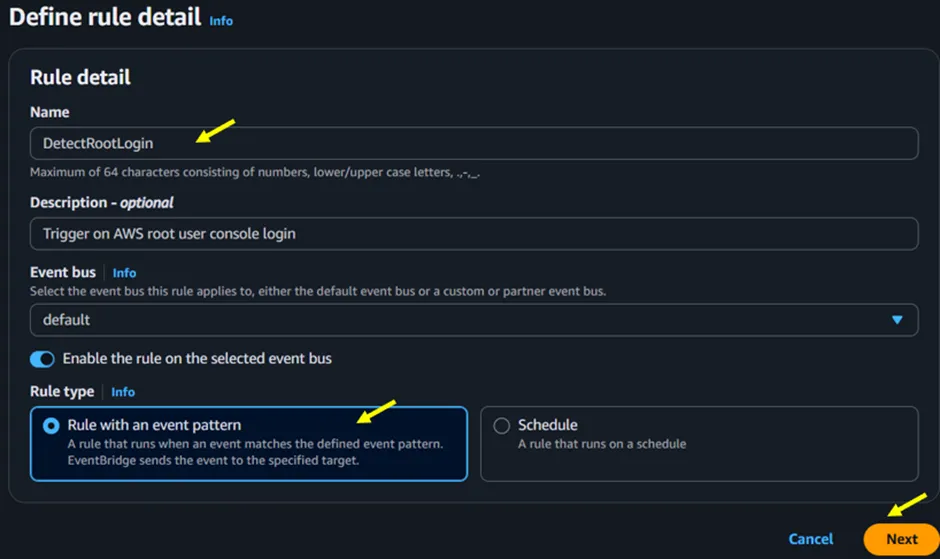 Figure 3.2
Figure 3.2
Under Event Pattern, select Custom pattern, then paste the JSON below.
{
"source": ["aws.signin"],
"detail-type": ["AWS Console Sign In via CloudTrail"],
"detail": {
"userIdentity": {
"type": ["Root"]
},
"eventName": ["ConsoleLogin"],
"responseElements": {
"ConsoleLogin": ["Success"]
}
}
}
This pattern matches only successful root account console logins.
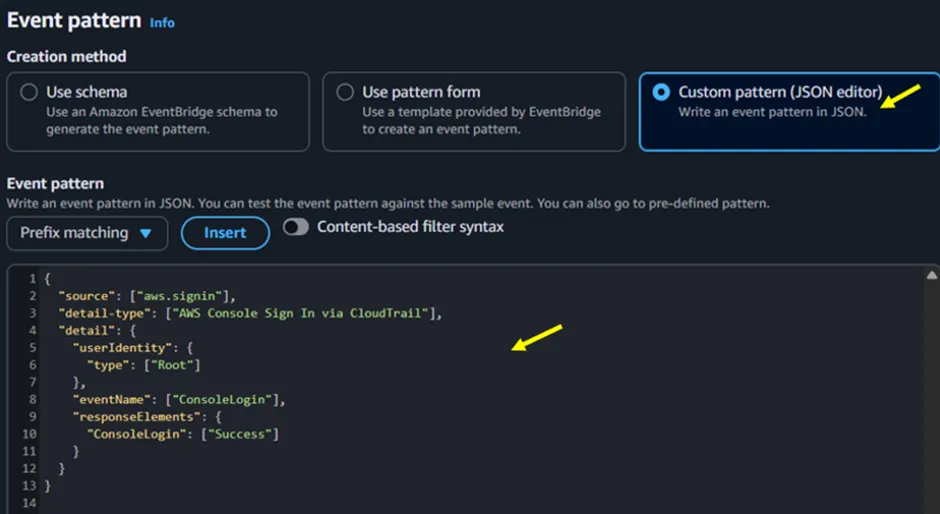 Figure 3.3
Figure 3.3
Click the Next button in Figure 3.4.
 Figure 3.4
Figure 3.4
In the Select Target screen (Figure 3.5), under select target(s) for target 1, select AWS Service. Then, under select a target, click on the dropdown button and select SNS Topic. Under the topic again, select the dropdown button and select the SNS topic you created earlier.
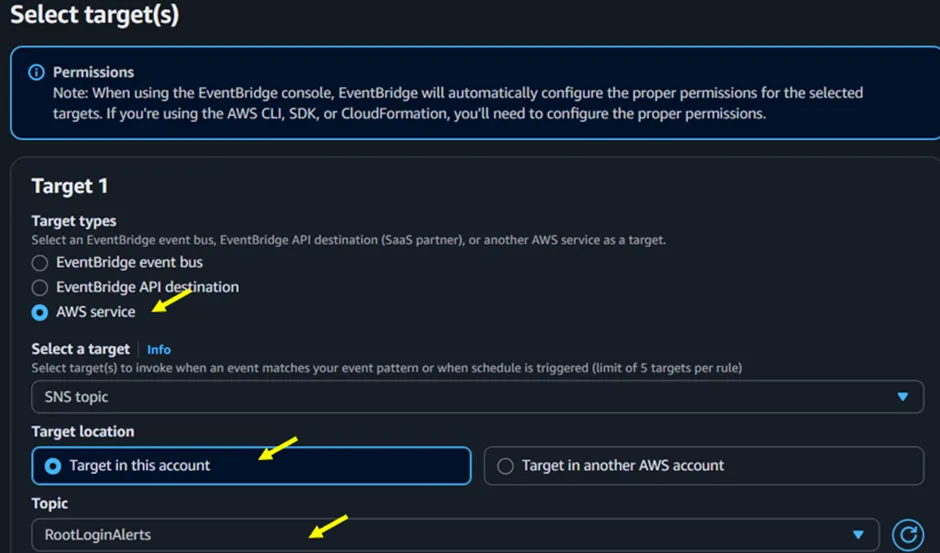 Figure 3.5
Figure 3.5
Under permission (Figure 3.6), select with the Use execution role (recommended), then click Next.
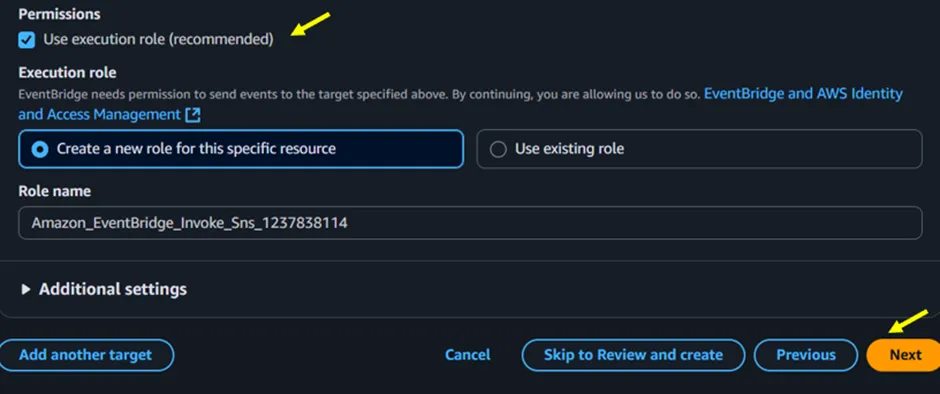 Figure 3.6
Figure 3.6
Leave tags as optional and click next.
 Figure 3.7
Figure 3.7
On the next page, preview and click on Create Rule.
 Figure 3.8
Figure 3.8
The Rule has been successfully created as shown below in Figure 3.9.
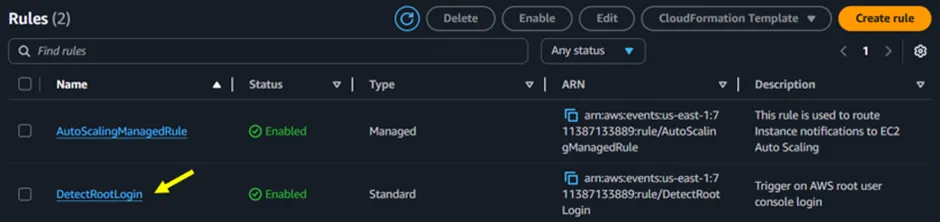 Figure 3.9
Figure 3.9
Step 4: Test Setup
- Log in to the AWS console using the root user.
- You should receive an email alert within seconds via SNS
I successfully logged into my AWS account with the root user credentials.
 Figure 3.9.1
Figure 3.9.1
Upon checking my email inbox, I received an alert notification indicating a successful root user login.
 Figure 3.9.2
Figure 3.9.2
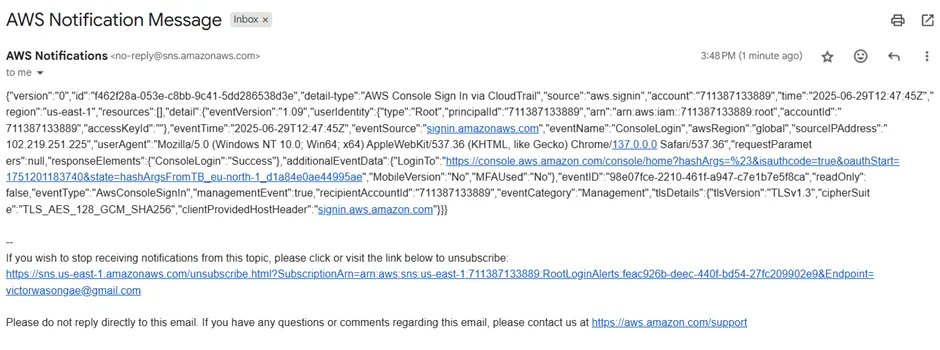 Figure 3.9.3
Figure 3.9.3
TIP
If you walked through this guide, don’t forget to delete your AWS resources that are no longer needed.
Recap: What We Accomplished
- CloudTrail detected the root user login as part of its management event logging.
- Amazon EventBridge matched the event using our custom rule targeting successful root logins.
- Amazon SNS immediately triggered an email alert to notify us of the activity in real-time.
Schedule Free Architecture Review
Conclusion
Keeping an eye on your AWS root account logins isn’t something you can skip; it’s vital. With Amazon EventBridge and SNS, you’ll get real-time, automated alerts when someone uses the root user to log in to your AWS account. This practical guide provides you with a quick, straightforward, and scalable solution using only AWS services.
Thanks for reading, and stay tuned for more.
