Complete Guide to Detecting Public Buckets with IAM Access Analyzer for S3
AWS S3 Security - Learn how to find and fix public S3 buckets using IAM Access Analyzer for S3

3 min read
While working at AWS as a Senior Security Solutions Architect, one of the most common potential security vulnerabilities I encountered within AWS accounts were AWS S3 buckets that either had public read access, public write access, or both. In this post, I’ll show you how to detect S3 buckets that are publicly accessible and how to fix this critical security issue.
Step 1 - Log into your AWS Account
Let’s first start by logging into your AWS Account and then searching for IAM Access analyzer for S3. Once you search for IAM Access analyzer you should see the option below in figure 1 to select.
Step 2 - IAM Access Analyzer for S3
Once you navigate to the IAM Access Analyzer for S3 service you will see a screen similar to the one in figure 1.1 below.
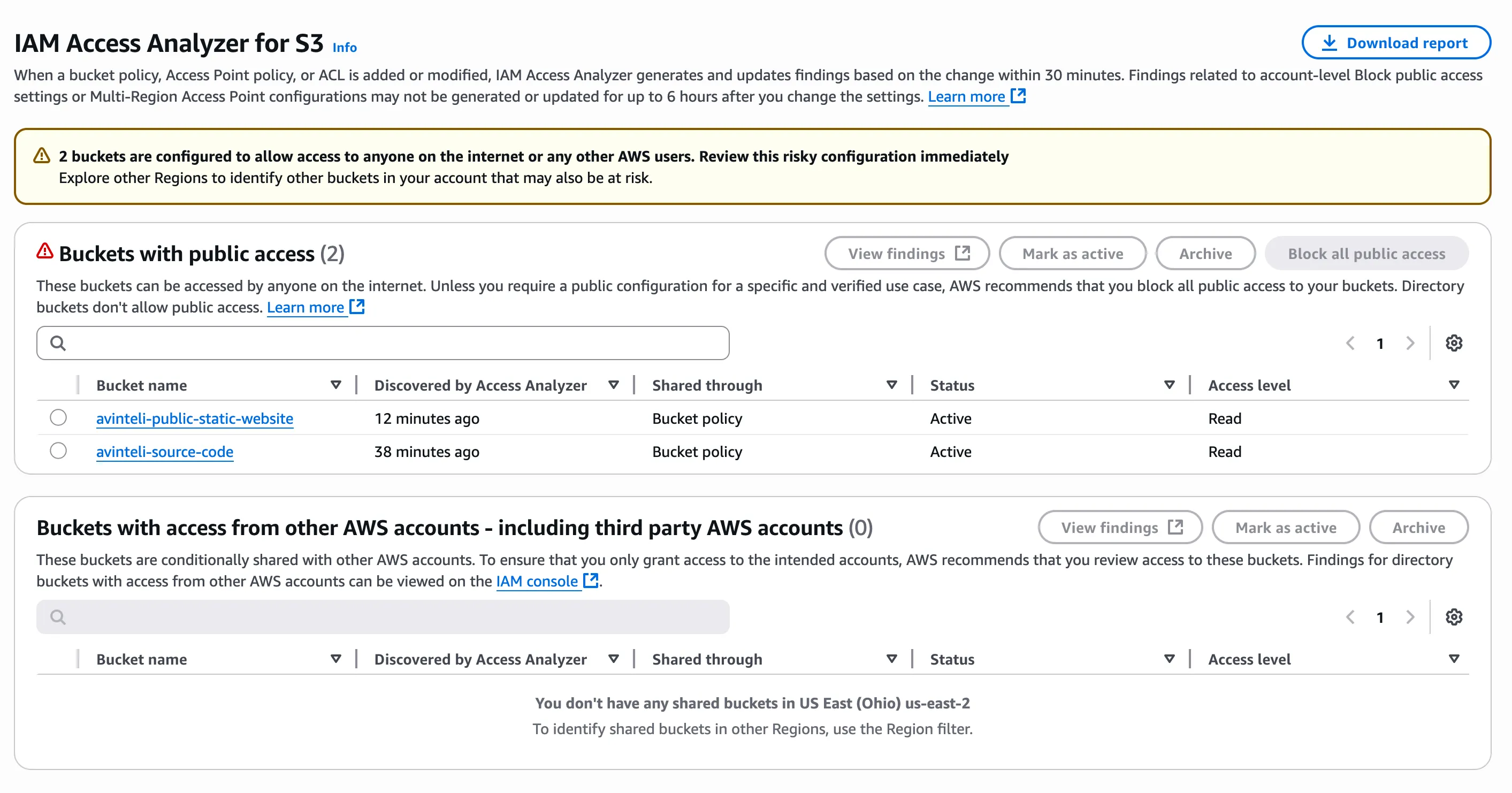 Figure 1.1
Figure 1.1
In this example, we can see the IAM Access Analyzer for S3 screen in figure 1.1, which shows two S3 buckets that have public Read access in our account.
The first bucket named avinteli-public-static-website has read access that is publicly available. Since AWS S3 allows you to host static websites that are publicly accessible, it is probably safe to ignore this S3 bucket that is being flagged.
The next S3 bucket named avinteli-source-code also has public read access. Based on the name of this bucket, it is likely storing some type of company software source code, and this probably should not be available publicly for people to download and read. Let’s now fix this security issue.
Step 3 - Block all public access
To fix this let’s start by selecting the radio button to the left of avinteli-source-code and then click the Block all public access button. See figure 1.2 below.
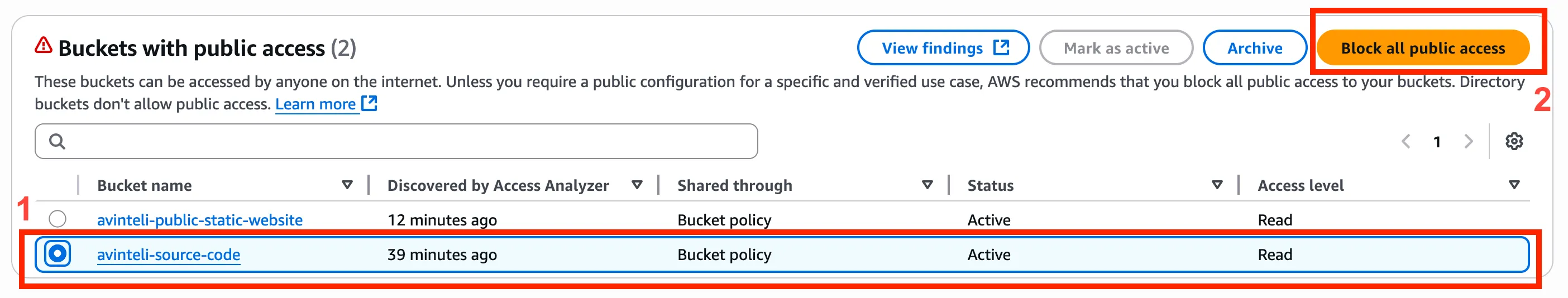 Figure 1.2
Figure 1.2
Once we have completed the steps in step 1 outlined above, we will see a screen confirming that public access to the specified S3 bucket has been blocked. See figure 1.3 below.
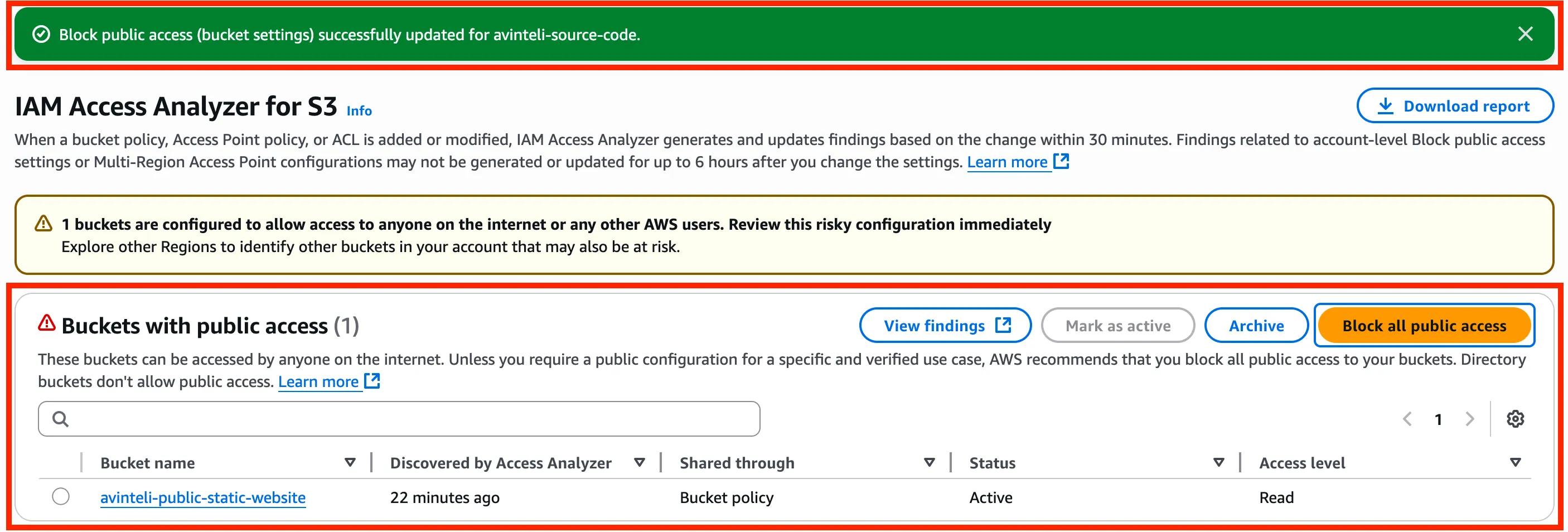 Figure 1.3
Figure 1.3
Schedule Free Architecture Review
Conclusion
And that is how easy it is to find public AWS S3 buckets with public access in your AWS accounts. All without ever having to navigate to the S3 service in the AWS Console, check bucket permissions, and make updates to individual buckets permissions. So, imagine if you have hundreds of S3 buckets in your AWS account and need to find which ones allow public access and the amount of time that would take to do manually. With IAM Access Analyzer you will save a lot of time by checking bucket access in one centralized location for open AWS S3 buckets.
Other Blogs
- About Author
Sheldon Sides
LinkedInSheldon is Founder and Chief Solutions Architect at Avinteli. Before founding Avinteli, he led Global Security and Compliance at Amazon Web Services (AWS) for Public Sector Partners and Global ISV Partners. Prior to his leadership role, he served as a Senior Security Solutions Architect at AWS, where he conducted comprehensive security assessments and guided Fortune 500 companies through complex, enterprise-scale AWS cloud implementations. His deep cloud security expertise and hands-on assessment experience help organizations identify critical vulnerabilities, close security gaps, accelerate their secure cloud adoption, and design and develop cloud-native solutions.
